90% of the Internet's top 200,000 HTTPS-enabled websites are vulnerable to known types of SSL (Secure Sockets Layer) attack, according to a report released Thursday by the Trustworthy Internet Movement (TIM), a nonprofit organization dedicated to solving Internet security, privacy and reliability problems.
The report is based on data from a new TIM project called SSL Pulse, which uses automated scanning technology developed by security vendor Qualys, to analyze the strength of HTTPS implementations on websites listed in the top one million published by Web analytics firm Alexa.
SSL Pulse checks what protocols are supported by the HTTPS-enabled websites (SSL 2.0, SSL 3.0, TLS 1.0, TLS 1.1, etc.), the key length used for securing communications (512 bits, 1024 bits, 2048 bits, etc.) and the strength of the supported ciphers (256 bits, 128 bits or lower).
The BEAST attack takes advantage of a flaw in SSL 3.0, allowing the attacker to grab and decrypt HTTPS cookies on an end user’s browser, effectively hijacking the victim’s session. This could be achieved either through an iframe injection or by loading the BEAST JavaScript into the victim’s browser, but BEAST is known to be especially hard to execute.
TIM has established a taskforce of security experts, who will review SSL governance issues and develop proposals aimed at fixing both SSL and the certificate authority systems, both of which have been called into question in recent times. In the case of certificate authorities (CAs), a number of them have been compromised in the past year, allowing attackers to spoof websites with fake certificates. One of those CAs, DigiNotar, went bankrupt after it was hacked.
90%25+SSL+sites+vulnerable+to+the+BEAST+SSL+attack
The attack was fixed in version 1.1 of the Transport Layer Security (TLS) protocol, but a lot of servers continue to support older and vulnerable protocols, like SSL 3.0, for backward compatibility reasons. Such servers are vulnerable to so-called SSL downgrade attacks in which they can be tricked to use vulnerable versions of SSL/TLS even when the targeted clients support secure versions.
The taskforce members include Michael Barrett, chief information security officer at PayPal; Taher Elgamal, one of the creators of the SSL protocol; Adam Langley, a Google software engineer responsible for SSL in Chrome and on the company's front-end servers; Moxie Marlinspike, the creator of the Convergence project, which offers an alternative method for SSL certificate validation; Ivan Ristic, the creator of the Qualys SSL Labs and Ryan Hurst, chief technology officer at certificate authority GlobalSign.
Monday, April 30, 2012
URL redirection Vulnerability in Google
An open redirect is a vulnerability that exists when a script allows redirectionto an external site by directly calling a specific URL in an unfiltered,unmanaged fashion, which could be used to redirect victims to unintended,malicious web sites. A web application accepts a user-controlled input that specifies a link to an external site, and uses that link in a Redirect.
A similar vulnerability is reported in Google by "Ucha Gobejishvili ( longrifle0x )". This problem may assist an attacker to conduct phishing attacks, trojan distribution, spammers.
Url: https://accounts.google.com/o/oauth2/auth?redirect_uri=http://www.something.com
Same vulnerability in Facebook, Discovered by ZeRtOx from Devitel group:
http://www.facebook.com/l.php?h=5AQH8ROsPAQEOTSTw7sgoW1LhviRUBr6iFCcj4C8YmUcC8A&u=www.something.com
Impact of Vulnerability :
The user may be redirected to an untrusted page that contains malware which may then compromise the user's machine. This will expose the user to extensive risk and the user's interaction with the web server may also be compromised if the malware conducts keylogging or other attacks that steal credentials, personally identifiable information (PII), or other important data.
The user may be subjected to phishing attacks by being redirected to an untrusted page. The phishing attack may point to an attacker controlled web page that appears to be a trusted web site. The phishers may then steal the user's credentials and then use these credentials to access the legitimate web site.
A similar vulnerability is reported in Google by "Ucha Gobejishvili ( longrifle0x )". This problem may assist an attacker to conduct phishing attacks, trojan distribution, spammers.
Url: https://accounts.google.com/o/oauth2/auth?redirect_uri=http://www.something.com
Same vulnerability in Facebook, Discovered by ZeRtOx from Devitel group:
http://www.facebook.com/l.php?h=5AQH8ROsPAQEOTSTw7sgoW1LhviRUBr6iFCcj4C8YmUcC8A&u=www.something.com
Impact of Vulnerability :
The user may be redirected to an untrusted page that contains malware which may then compromise the user's machine. This will expose the user to extensive risk and the user's interaction with the web server may also be compromised if the malware conducts keylogging or other attacks that steal credentials, personally identifiable information (PII), or other important data.
The user may be subjected to phishing attacks by being redirected to an untrusted page. The phishing attack may point to an attacker controlled web page that appears to be a trusted web site. The phishers may then steal the user's credentials and then use these credentials to access the legitimate web site.
International Police Association Website Defaced By Hackers
Anonymous hackers deface International Police Association http://ipa-iac.org (IPA) on Friday afternoon and Anonymous hackers responsible left an angry message on the website's homepage, stating that they defaced the page "for the lulz" (for fun) but also warned that they might have stolen some "sensitive data."
A message posted at the top of the page reads, "oHai [hello]... International Police Association (International Admin Center) you will see we haz [had] some #LULZ at your expense maybe you will fix your security issues and of course... we always recommend you NOT store admin passwords in PLAINTEXT For a site like International Police Association... w3 [we] really expected moar [more]... #LULZ the thin..."
The International Police Association is the largest organization for police officers in the world according to Wikipedia, and is not connected to Interpol http://www.interpol.int/ . The IPA was founded by English police sergeant Arthur Troop in January 1950 under the model "Service Through Friendship" with the goal of creating friendly links to encourage cooperation between police officers across the world. The organization currently has around 400,000 members in 64 countries. Its main offices are based in Nottingham, England.
The message continues to boast that Anonymous cannot be stopped because "There is no head to cut off motherfu--kers!!!" Before concluding with the words, " F--k the police!!!!"
A message posted at the top of the page reads, "oHai [hello]... International Police Association (International Admin Center) you will see we haz [had] some #LULZ at your expense maybe you will fix your security issues and of course... we always recommend you NOT store admin passwords in PLAINTEXT For a site like International Police Association... w3 [we] really expected moar [more]... #LULZ the thin..."
The International Police Association is the largest organization for police officers in the world according to Wikipedia, and is not connected to Interpol http://www.interpol.int/ . The IPA was founded by English police sergeant Arthur Troop in January 1950 under the model "Service Through Friendship" with the goal of creating friendly links to encourage cooperation between police officers across the world. The organization currently has around 400,000 members in 64 countries. Its main offices are based in Nottingham, England.
The message continues to boast that Anonymous cannot be stopped because "There is no head to cut off motherfu--kers!!!" Before concluding with the words, " F--k the police!!!!"
Facebook Source Code Hacker Explains ,What Really Happened !!!!!!!
Software development student Glenn Mangham, 26, was freed earlier this month after appeal judges halved the eight-month prison sentence he was given for infiltrating and nearly bringing down the multi-million-dollar site.
Glenn Mangham, of York, England, posted a lengthy writeup on his blog and a video, saying that he accepts full responsibility for his actions and that he did not think through the potential ramifications.
"Strictly speaking what I did broke the law because at the time and subsequently it was not authorised," Mangham wrote. "I was working under the premise that sometimes it is better to seek forgiveness than to ask permission."
Mangham implied he meant to contact Facebook once he had noticed the social-networking site had observed his intrusions, which he did little to hide. He didn't use proxy servers because he said it made auditing take longer due to the time delay between each request made to a server. He was also hoping that even when he got caught, Facebook would let him off the hook.
Mangham was sentenced to eight months in prison in February, but the sentence was reduced to four months by an appeals court earlier this month. He was then eligible for release, subject to electronic monitoring and restrictions on his internet use.
Mangham portrayed himself as a security researcher who continued to probe Facebook because he wanted to look deeper for other security issues, since most systems have "a tough outer shell and a soft inside." He wrote that in the past he had been paid by Yahoo for finding vulnerabilities.
Mangham's copy of the source code would surely have been of interest to cybercriminals who attempt to use Facebook to perpetuate scams. But he wrote he had no intention of selling the code.
Software development student Glenn Mangham, 26, was freed earlier this month after appeal judges halved the eight-month prison sentence he was given for infiltrating and nearly bringing down the multi-million-dollar site.
Glenn Mangham, of York, England, posted a lengthy writeup on his blog and a video, saying that he accepts full responsibility for his actions and that he did not think through the potential ramifications.
"Strictly speaking what I did broke the law because at the time and subsequently it was not authorised," Mangham wrote. "I was working under the premise that sometimes it is better to seek forgiveness than to ask permission."
Mangham implied he meant to contact Facebook once he had noticed the social-networking site had observed his intrusions, which he did little to hide. He didn't use proxy servers because he said it made auditing take longer due to the time delay between each request made to a server. He was also hoping that even when he got caught, Facebook would let him off the hook.
Mangham was sentenced to eight months in prison in February, but the sentence was reduced to four months by an appeals court earlier this month. He was then eligible for release, subject to electronic monitoring and restrictions on his internet use.
Mangham portrayed himself as a security researcher who continued to probe Facebook because he wanted to look deeper for other security issues, since most systems have "a tough outer shell and a soft inside." He wrote that in the past he had been paid by Yahoo for finding vulnerabilities.
Mangham's copy of the source code would surely have been of interest to cybercriminals who attempt to use Facebook to perpetuate scams. But he wrote he had no intention of selling the code.
Glenn Mangham, of York, England, posted a lengthy writeup on his blog and a video, saying that he accepts full responsibility for his actions and that he did not think through the potential ramifications.
"Strictly speaking what I did broke the law because at the time and subsequently it was not authorised," Mangham wrote. "I was working under the premise that sometimes it is better to seek forgiveness than to ask permission."
Mangham implied he meant to contact Facebook once he had noticed the social-networking site had observed his intrusions, which he did little to hide. He didn't use proxy servers because he said it made auditing take longer due to the time delay between each request made to a server. He was also hoping that even when he got caught, Facebook would let him off the hook.
Mangham was sentenced to eight months in prison in February, but the sentence was reduced to four months by an appeals court earlier this month. He was then eligible for release, subject to electronic monitoring and restrictions on his internet use.
Mangham portrayed himself as a security researcher who continued to probe Facebook because he wanted to look deeper for other security issues, since most systems have "a tough outer shell and a soft inside." He wrote that in the past he had been paid by Yahoo for finding vulnerabilities.
Mangham's copy of the source code would surely have been of interest to cybercriminals who attempt to use Facebook to perpetuate scams. But he wrote he had no intention of selling the code.
Software development student Glenn Mangham, 26, was freed earlier this month after appeal judges halved the eight-month prison sentence he was given for infiltrating and nearly bringing down the multi-million-dollar site.
Glenn Mangham, of York, England, posted a lengthy writeup on his blog and a video, saying that he accepts full responsibility for his actions and that he did not think through the potential ramifications.
"Strictly speaking what I did broke the law because at the time and subsequently it was not authorised," Mangham wrote. "I was working under the premise that sometimes it is better to seek forgiveness than to ask permission."
Mangham implied he meant to contact Facebook once he had noticed the social-networking site had observed his intrusions, which he did little to hide. He didn't use proxy servers because he said it made auditing take longer due to the time delay between each request made to a server. He was also hoping that even when he got caught, Facebook would let him off the hook.
Mangham was sentenced to eight months in prison in February, but the sentence was reduced to four months by an appeals court earlier this month. He was then eligible for release, subject to electronic monitoring and restrictions on his internet use.
Mangham portrayed himself as a security researcher who continued to probe Facebook because he wanted to look deeper for other security issues, since most systems have "a tough outer shell and a soft inside." He wrote that in the past he had been paid by Yahoo for finding vulnerabilities.
Mangham's copy of the source code would surely have been of interest to cybercriminals who attempt to use Facebook to perpetuate scams. But he wrote he had no intention of selling the code.
Friday, April 27, 2012
Cyber War : Another 7000 Israel credit cards Exposed on Internet
This week has began under worse auspices worse for Israel, which, despite its attention to the cyber threats posed by cyber-space, has been victim of a series of attacks that have checkmated the government of Jerusalem.
Kosova Hacker's Security Group of Hackers today claim to release another Another 7000 Israel credit cards on Internet. Last week xOmar from "group-xp" threatened the Israeli people by exposing millions of credit cards. After that Israel said that it will respond to cyber-attacks in the same way it responds to violent terrorist acts, by striking back with force against hackers who threaten the Jewish state.
The Dump of these 7000 Cards are posted on Tinypaste by Kisova Hackers. Th3 Dir3ctorY, ThEtA.Nu, & X|CRIPO, three hackers from Kosova Hacker's Security Group posted all the credentials including full name of the card holder, CCV, card no, expiry date.
More, Saudi cyber Hacker OxOmar struck again last Monday by disrupted the websites of Israel's stock exchange and National air carrier. Israel is facing with a true escalation in cyberwar. Another Interesting Read on Israel Cyber war by Pierluigi Paganini on his Blog.
Chinese Hackers Continued To Attack Phillipine
Hackers continued to attack the Philippine government's online presence, with at least one agency on Thursday reporting a denial-of-service attack the night before.
The official website of the Department of Budget and Management (DBM) yesterday became the latest victim of a cyber attack by suspected Chinese hackers.The DBM website was defaced at around 2 pm Wednesday and will remain offline until the repairs are complete, according to Budget Secretary Florencio Abad.
In a press statement, Abad said the DBM's official website, www.dbm.gov.ph, is currently undergoing a security audit and "may be inaccessible until critical issues are resolved."
The hackers placed a Chinese flag on the DBM website along with a caption announcing it was “Hacked! Owned by Chinese Hackers?!”
The webpage also contained a message: “How come a small bitch border country are overconfident? And Challenged to Our Chinese Super Hacker?” A warning was also displayed: “Don’t Trouble Chinese, Don’t Play with Fire.”
The message indicated that those who defaced the DBM website are the same ones who attacked the Vietnamese government's website, gov.vn.
The cyberattacks on Filipino websites began last Sunday when the website of the University of the Philippines was taken down. The hackers claimed that they took down UP's website as an expression of displeasure over Manila's claim that it owns the Scarborough (Panatag) Shoal. In retaliation, groups who identified themselves as Filipino hackers also launched an attack on a number Chinese websites.
The Department of Foreign Affairs has condemned the series of cyberattacks on both Chinese and Filipino websites, saying these attacks would only worsen the tension between Manila and Beijing.
In reaction, Filipino hackers launched a series of attacks on Chinese websites starting Monday. In an operation dubbed "#OpChinaDown," Filipinos attacked the following websites:
http://www.ocex.com.cn
http://www.teawindow.com
http://www.higvod.cn
http://www.lzrk.gov.cn
http://lppm.bigc.edu.cn/Pr1vX.htm
http://xxb.leiyang.gov.cn/Pr1vX.htm
http://en.founder.com.cn
http://dxswl.cn
http://www.cord.cn
http://fmprc.gov.cn
http://www.3322.net.cn
http://wahsangtech.com/index.aspx
The attacks came as the Palace pleaded to both Filipinos and Chinese to stop attacking each other in cyber space in light of the two countries’ current conflict over Panatag Shoal
Iran Preparing For Cyberwar Against U.S
Security professionals in both the U.S. government and in private industry have long feared the prospect of a cyberwar with China or Russia, two states capable of launching destructive attacks on the computer networks that control critical assets such as the power grid or the financial system.
But, Iran is recruiting a hacker army to target the U.S. power grid, water systems and other vital infrastructure for cyberattack in a future confrontation with the United States, security specialists will warn Congress Thursday.
“If Iran is willing to blow up a Washington restaurant and kill innocent Americans, we would be naive to think Iran would never conduct a cyberattack against the U.S. homeland,” said Counterterrorism and Intelligence Subcommittee Chairman Pat Meehan, R-Pa.
“Over the past three years, the Iranian regime has invested heavily in both defensive and offensive capabilities in cyberspace,” states testimony from Ilan Berman, vice president of the hawkish American Foreign Policy Council, in his remarks for Thursday’s hearing.
“For the Iranian regime the conclusion drawn from Stuxnet is clear: War with the West, at least on the cyberfront, has already been joined, and the Iranian regime is mobilizing,” states Mr. Berman.
U.S. intelligence officials declined to comment further on Iranian cyber capabilities, though they acknowledge the threat in general terms.
How To Make Money By Watching Youtube Videos
Most people don't know it's possible to watch youtube videos and earn
money whilst doing so, i'll keep this hub short as there's not an awful
lot to explain but i'll explain everything in detail!
First of you're going to need a YouTube account which you probably already have if not go to YouTube and get one.
When you have your YouTube account set up visit Paid2Youtube and set an account up with them, you recieve 1c per video you watch, 10c for every comment and 35c every time you subscribe to a YouTube account.
First of you're going to need a YouTube account which you probably already have if not go to YouTube and get one.
When you have your YouTube account set up visit Paid2Youtube and set an account up with them, you recieve 1c per video you watch, 10c for every comment and 35c every time you subscribe to a YouTube account.
Thursday, April 26, 2012
DNSChanger: FBI Warns Infected Computers Will Lose Internet & Email Access in July
 DNS (Domain Name System) is an Internet service that converts user-friendly domain names into the numerical Internet protocol (IP) addresses that computers use to talk to each other. When you enter a domain name, such as www.fbi.gov, in your web browser address bar, your computer contacts DNS servers to determine the IP address for the website. Your computer then uses this IP address to locate and connect to the website. DNS servers are operated by your Internet service provider (ISP) and are included in your computer’s network configuration. DNS and DNS Servers are a critical component of your computer’s operating environment—without them, you would not be able to access websites, send e-mail, or use any other Internet services.
DNS (Domain Name System) is an Internet service that converts user-friendly domain names into the numerical Internet protocol (IP) addresses that computers use to talk to each other. When you enter a domain name, such as www.fbi.gov, in your web browser address bar, your computer contacts DNS servers to determine the IP address for the website. Your computer then uses this IP address to locate and connect to the website. DNS servers are operated by your Internet service provider (ISP) and are included in your computer’s network configuration. DNS and DNS Servers are a critical component of your computer’s operating environment—without them, you would not be able to access websites, send e-mail, or use any other Internet services.Criminals have learned that if they can control a user’s DNS servers, they can control what sites the user connects to on the Internet. By controlling DNS, a criminal can get an unsuspecting user to connect to a fraudulent website or to interfere with that user’s online web browsing. One way criminals do this is by infecting computers with a class of malicious software (malware) called DNSChanger. In this scenario, the criminal uses the malware to change the user’s DNS server settings to replace the ISP’s good DNS servers with bad DNS servers operated by the criminal. A bad DNS server operated by a criminal is referred to as a rogue DNS server.
Working with Estonian officials, the FBI was able to track down the perps — six Estonian nationals were arrested for the crime last November — and seize their servers. But given the number of computers estimated infected, the FBI opted to leave the servers running, ad-neutralized, to avoid disrupting Internet functionality for those unaware their computers were compromised. And to give users more time to purge, the FBI secured a court order on March 12, 2012 that authorized the Internet Systems Consortium (ISC) — a nonprofit corporation that supports the Internet’s infrastructure — to roll out and maintain temporary “clean” DNS servers. But since these servers cost money to operate, the plan has been to shut them off on July 9, 2012. When that happens, DNS-related Internet activity on infected computers, e.g. web and email, will cease to function.
To be clear, your Internet service itself will be unaffected by the change: If your computer is infected with the DNSChanger malware, your Internet router will keep routing and any commands sent by your computer that aren’t DNS-related will still pass. The FBI isn’t shutting off Internet service to impacted machines, it’s just pulling the plug on a stopgap measure designed to bandaid the broken process currently facilitating DNS communication on infected machines.
It is quite possible that computers infected with this malware may also be infected with other malware. The establishment of these clean DNS servers does not guarantee that the computers are safe from other malware. The main intent is to ensure users do not lose DNS services.
What Does DNSChanger Do to My Computer?
DNSChanger malware causes a computer to use rogue DNS servers in one of two ways. First, it changes the computer’s DNS server settings to replace the ISP’s good DNS servers with rogue DNS servers operated by the criminal. Second, it attempts to access devices on the victim’s small office/home office (SOHO) network that run a dynamic host configuration protocol (DHCP) server (eg. a router or home gateway). The malware attempts to access these devices using common default usernames and passwords and, if successful, changes the DNS servers these devices use from the ISP’s good DNS servers to rogue DNS servers operated by the criminals. This is a change that may impact all computers on the SOHO network, even if those computers are not infected with the malware.
Am I Infected?
The best way to determine if your computer or SOHO router has been affected by DNSChanger is to have them evaluated by a computer professional.
To determine if a computer is using rogue DNS servers, it is necessary to check the DNS server settings on the computer. An industry wide team has developed an easy “are you infected” web site, a quick way to determine if you are infected with DNSChanger. The site is designed for any normal computer user to check for the DNSChanger infection.*
After clicking the link below you will be presented with one of two screens:
 PASS - Most likely not infected |  FAIL - Infected |
What Is DNS Changer Malware And What Doest It Do
What is the DNS Changer Malware?
What does the DNS Changer Malware do?
Under a court order, expiring July 9, the Internet Systems Consortium is operating replacement DNS servers for the Rove Digital network. This will allow affected networks time to identify infected hosts, and avoid sudden disruption of services to victim machines.
DNS Changer Virus: FBI Removal Tips & How To Check If You’ve Got Malware

People are starting to pay attention to the information about the DNSChanger Virus that has infected hundreds of thousands of systems in the United States and around the world. There could be up to 4 million infected hosts throughout the world.
On July 9th, 2012 if you haven’t checked your system for the DNS Changer Virus and you have it, you will not be able to use the Internet. The effected systems are Windows or Mac systems. This means that if you access the Internet from an iOS device, Linux or from an Android OS device you’re good to go and are not infected.
So why won’t your computer be able to access the Internet if you have the DNS Changer Malware? Your DNS settings are changed by the virus rerouting you to hijacked servers that serve ads from the hackers that have amassed millions in ad dollars. The FBI took over these hijacked servers and have started making people’s computers infected by the virus go to destinations without ads.
The government can’t afford to continue to operate all of these servers so they’re turning them off on July 9th, 2012 and at that point infected computers will be trying to access a server that doesn’t exist.
So let’s get the DNS Changer Virus removed from your system. We have provided some videos below to walk you through how to get it removed from your system as well as resources from the FBI Removal page that describes what actions you can take.
The information on the FBI page that is called Check To See if Your Computer is Using a Rogue DNS states:
“The FBI is seeking information from individuals, corporate entities, and Internet Services Providers who believe that they have been victimized by malicious software (“malware”) related to the defendants. This malware modifies a computer’s Domain Name Service (DNS) settings and thereby directs the computers to receive potentially improper results from rogue DNS servers hosted by the defendants.If you believe you have been victimized in this case, please type your DNS information into the search box below.
Information on how to determine your DNS settings, along with other technical details about DNSChanger, can be found at www.fbi.gov/news/stories/2011/november/malware_110911/dns-changer-malware.pdf.”
The easiest way to check if you’ve got the DNSChanger Malware is to go to:
http://www.dns-ok.usIf you see a screen that looks like our above graphic you are good to go. You should still probably get some anti-virus software and malware removal software to remove any spy programs or hidden trojans on your PC. When issues like the DNS Changer virus come up it’s always a good reminder to make sure you’re protected and your computer is safe from hackers.
There are popular products that will protect your computer all the time from viruses, trojans, spy programs and a lot more. Some of the best rated products are created by companies like Kaspersky and Norton. Kaspersky Internet Security 2012 and Norton Internet Security 2012 are quick to download and will provide you with premium protection from just about anything you might run into.
Virus hits internet today (SLCERT)
A destructive virus has hit the internet, Sri Lanka Computer Emergency Response Team(SLCERT) issued a warning today. When a computer is infected with the particular malware; DNS Changer, it is reported to change the Domain Name Server (DNS) settings of the computer making way to divert traffic to unsolicited and potentially illegal websites. However, SLCERT is yet to receive complaints in this regard. To protect computers from potential DNS Changer threats,SLCERT advises users to go to http://www.dcwg.org/detect.
VMWare Source Code leaked by Anonymous Hackers
VMware on Tuesday announced that a single file from its ESX server hypervisor source code has been posted online, and it held out the possibility that more proprietary files could be leaked in the future. "The fact that the source code may have been publicly shared does not necessarily mean that there is any increased risk to VMware customers," VMware said in a statement.
"Hardcore Charlie" - who claims to have downloaded some 300 Megabytes of VMWare source code.
Anonymous tweeted:
@AnonymousIRC: Oops, VMWare source leaked? Not good http://pastebin.com/JGxdK6vw to Anonymous contributors. May the Pirate Bay always sail strong!
The leaked documents include what appear to be internal VMWare communications, pasted onto CEIEC letterhead and with official looking stamps. One email exchange, dated June 5, 2003 is from Jeffrey Sheldon to an internal VMWare listserv and has the subject "code review:untruncating segments.
Given the large number of service providers that run vSphere, security issues in ESX could potentially have a broad and widespread impact, according to security researchers. VMware says it is looking into the matter and will be canvassing its industry partners and developers in order to determine the source of the breach.
"Hardcore Charlie" - who claims to have downloaded some 300 Megabytes of VMWare source code.
Anonymous tweeted:
@AnonymousIRC: Oops, VMWare source leaked? Not good http://pastebin.com/JGxdK6vw to Anonymous contributors. May the Pirate Bay always sail strong!
The leaked documents include what appear to be internal VMWare communications, pasted onto CEIEC letterhead and with official looking stamps. One email exchange, dated June 5, 2003 is from Jeffrey Sheldon to an internal VMWare listserv and has the subject "code review:untruncating segments.
Given the large number of service providers that run vSphere, security issues in ESX could potentially have a broad and widespread impact, according to security researchers. VMware says it is looking into the matter and will be canvassing its industry partners and developers in order to determine the source of the breach.
Hackers Launch DDoS Attack on D.C. Government Websites
Hackers launched a DoS denial of service attack on D.C. government websites today, clogging the system with a flurry of requests so that it operates extremely slow or is impossible to load.
“The District government has detected an attempted intrusion into it’s technology infrastructure system,” the D.C. Department of Homeland Security and Emergency Management said in an email to specified recipients around noon.
“Customers may experience intermittent difficulties in accessing the District’s web site as we attempt to address the issue. We are aggressively working to resolve this matter.”
In January the group launched a similar attack against the UFC for its support of the controversial Stop Online Piracy Act that was debated by Congress earlier this year. DDoS attacks have been launched by a variety of groups such as Anonymous and LulzSec against federal government websites and servers, including the FBI and CIA.
“The District government has detected an attempted intrusion into it’s technology infrastructure system,” the D.C. Department of Homeland Security and Emergency Management said in an email to specified recipients around noon.
“Customers may experience intermittent difficulties in accessing the District’s web site as we attempt to address the issue. We are aggressively working to resolve this matter.”
In January the group launched a similar attack against the UFC for its support of the controversial Stop Online Piracy Act that was debated by Congress earlier this year. DDoS attacks have been launched by a variety of groups such as Anonymous and LulzSec against federal government websites and servers, including the FBI and CIA.
Tuesday, April 24, 2012
Stop CISPA - Stop censoring Internet !
The Cyber Intelligence Sharing and Protection Act (CISPA) H.R. 3532 is a new bill being introduced in Congress that is gunning to blast the ongoing cyber attacks that have occurred since internet users figured out the keyboard could be an effective weapon. If passed through Congress, the bill would allow the government access to personal correspondence of any person of their choosing. Once again, we are being fucked by those nosey neighbors in our government.
You should be very mad and very afraid because CISPA is far worse than SOPA and PIPA in its effects on the internet. The wording of this bill is mumbo jumbo, vague and broad. Reading through the nonsense, basically the act would allow Congress to circumvent existing exemptions to online privacy laws, and would allow the monitoring and censorship of any user of the internet. Peeping Toms will be wetting their pants. The real kicker (in our asses) is that it will also allow the government to stop online communications which they deem critical or disruptive to them. They can even decide they don’t like what you say about other private parties and shut you down.
The Center for Democracy and Technology states that CISPA would allow Internet Service Providers (ISPs) to “funnel private communications and related information back to the government without adequate privacy protections and controls. The bill does not specify which agencies ISPs could disclose customer data to, but the structure and incentives in the bill raise a very real possibility that the National Security Agency or the DOD’s Cybercommand would be the primary recipient.” Holy Bejeezers, where are Batman and Robin when you need them?
What will happen if we don’t stop CISPA?
CISPA effectively creates an exemption to all existing internet privacy laws. Pay attention here, because this means the government will have control over the entire internet, and would be able to censor anything they deem as a “threat” to national security. And what do those ding dongs deem a threat? Well, that is up for them to decide. With the power they would have, it would enable them to interpret anything as a potential “threat” if they really wanted to. Be afraid, very, very, very afraid.
This is just another trap to have our freedom stripped away even further. It is blaringly obvious that our very own government has slowly diminished the very freedoms we were promised at the inception of this “democracy.” It is painful that it may not appear obvious that each new bill that is introduced and passed in Congress contains many clauses that most Americans aren’t even aware of. This is why it is imperative we examine each new bill and law very closely. It is a shameful fact we have to protect ourselves from the very institution we pay to work in our best interest.
It blows my mind that social networks like Facebook support CISPA. Who is paying who off? Here is what Joel Kaplan, FB Vice President said was the reason they support the bill.
“One challenge we and other companies have had is in our ability to share information with each other about cyber attacks. When one company detects an attack, sharing information about that attack promptly with other companies can help protect those other companies and their users from being victimized by the same attack,” Kaplan wrote a blog post on Friday. “Similarly, if the government learns of an intrusion or other attack, the more it can share about that attack with private companies (and the faster it can share the information), the better the protection for users and our systems.”
Umm, what am I missing here? You need an anti-privacy law to get off your duff and let others know if you are being attacked? It is all to crazy making and once again we have to mobilize and put the pressure needed on our government to dump this dumb bill.
You should be very mad and very afraid because CISPA is far worse than SOPA and PIPA in its effects on the internet. The wording of this bill is mumbo jumbo, vague and broad. Reading through the nonsense, basically the act would allow Congress to circumvent existing exemptions to online privacy laws, and would allow the monitoring and censorship of any user of the internet. Peeping Toms will be wetting their pants. The real kicker (in our asses) is that it will also allow the government to stop online communications which they deem critical or disruptive to them. They can even decide they don’t like what you say about other private parties and shut you down.
The Center for Democracy and Technology states that CISPA would allow Internet Service Providers (ISPs) to “funnel private communications and related information back to the government without adequate privacy protections and controls. The bill does not specify which agencies ISPs could disclose customer data to, but the structure and incentives in the bill raise a very real possibility that the National Security Agency or the DOD’s Cybercommand would be the primary recipient.” Holy Bejeezers, where are Batman and Robin when you need them?
What will happen if we don’t stop CISPA?
CISPA effectively creates an exemption to all existing internet privacy laws. Pay attention here, because this means the government will have control over the entire internet, and would be able to censor anything they deem as a “threat” to national security. And what do those ding dongs deem a threat? Well, that is up for them to decide. With the power they would have, it would enable them to interpret anything as a potential “threat” if they really wanted to. Be afraid, very, very, very afraid.
This is just another trap to have our freedom stripped away even further. It is blaringly obvious that our very own government has slowly diminished the very freedoms we were promised at the inception of this “democracy.” It is painful that it may not appear obvious that each new bill that is introduced and passed in Congress contains many clauses that most Americans aren’t even aware of. This is why it is imperative we examine each new bill and law very closely. It is a shameful fact we have to protect ourselves from the very institution we pay to work in our best interest.
It blows my mind that social networks like Facebook support CISPA. Who is paying who off? Here is what Joel Kaplan, FB Vice President said was the reason they support the bill.
“One challenge we and other companies have had is in our ability to share information with each other about cyber attacks. When one company detects an attack, sharing information about that attack promptly with other companies can help protect those other companies and their users from being victimized by the same attack,” Kaplan wrote a blog post on Friday. “Similarly, if the government learns of an intrusion or other attack, the more it can share about that attack with private companies (and the faster it can share the information), the better the protection for users and our systems.”
Umm, what am I missing here? You need an anti-privacy law to get off your duff and let others know if you are being attacked? It is all to crazy making and once again we have to mobilize and put the pressure needed on our government to dump this dumb bill.
zDefender - Enterprise smartphone IDS/IPS released by Zimperium
Do you recall the security firm Zimperium which came out with ANTI, the killer Android app that allowed even the clueless to hack and pwn like a pentester?
Zimperium, an Israeli security start up founded by Zuk Avraham, a world-renowned hacker and security researcher, has debuted its latest product, the zDefender at DEMO in Santa Clara, California.
Called zDefender, this product can detect malicious attacks and take proactive measures to reduce threats via automatic preventive traffic filters and a remote management console.
With the onslaught of mobile malware, everyone should have antivirus up and running immediately after purchasing a smartphone. You’d think you were protected from various attacks like man in the middle (MITM) attacks ? At DEMO Spring 2012, Zuk planted 2 Routers, providing 3 Access points, which have claimed about 3,000 mobile device victims so far.
zDefender is able to do this by using Zimperium's patent-pending zCore technology. These preventive actions are robust and seamless to the user, and enable even the least sophisticated users in any organization to protect themselves from inadvertent attacks. This functionality may be offered on a modular basis, depending on the vertical market and specific customer requirements.
As you can see in the video below when Zimperium announced zDefender, Zuk explains that antivirus is a normal app that runs on the same permission level as malware. Once malware infects your device’s memory, the malware elevates its privileges until it’s higher than the antivirus. “Once a malware has infected your phone, any existing solution will not help, and it’s simply game over.”
Zimperium, an Israeli security start up founded by Zuk Avraham, a world-renowned hacker and security researcher, has debuted its latest product, the zDefender at DEMO in Santa Clara, California.
Called zDefender, this product can detect malicious attacks and take proactive measures to reduce threats via automatic preventive traffic filters and a remote management console.
With the onslaught of mobile malware, everyone should have antivirus up and running immediately after purchasing a smartphone. You’d think you were protected from various attacks like man in the middle (MITM) attacks ? At DEMO Spring 2012, Zuk planted 2 Routers, providing 3 Access points, which have claimed about 3,000 mobile device victims so far.
zDefender is able to do this by using Zimperium's patent-pending zCore technology. These preventive actions are robust and seamless to the user, and enable even the least sophisticated users in any organization to protect themselves from inadvertent attacks. This functionality may be offered on a modular basis, depending on the vertical market and specific customer requirements.
As you can see in the video below when Zimperium announced zDefender, Zuk explains that antivirus is a normal app that runs on the same permission level as malware. Once malware infects your device’s memory, the malware elevates its privileges until it’s higher than the antivirus. “Once a malware has infected your phone, any existing solution will not help, and it’s simply game over.”
Specialized Trojan can stealing credit card details from hotel
The next time you check in to a hotel, a cybercriminal could be checking you out. A remote access computer Trojan (RAT) designed to steal credit card details from hotel point-of-sale (PoS) applications is being sold on the underground forums, according to researchers from security firm Trusteer.
Trusteer, the world’s leading provider of secure web access services, detected these schemes and says hotel poaching is a virile trade in underground and tech forums. Attack codes can be purchased in Visa underground forums for $280 and the spyware cannot be detected by anti-virus software. The package even includes a manual loaded with tips on how the poacher can trick the desk clerk into loading the spyware for them.
Malware writers often repackage their malicious installers with new algorithms in order to evade signature-based antivirus detection, said Bogdan Botezatu, a senior e-threat analyst at antivirus vendor BitDefender.
"The fact that the RAT's creator decided to target the hospitality industry is consistent with a recently observed change in the focus of cybercriminals - an expansion from online banking attacks to attacks against PoS systems, Criminals are increasingly expanding the focus of their attacks from online banking targets to enterprises," said Trusteer's CTO Amit Klein.
While this credit card scam seems nearly impossible to detect and prevent, you can keep your finances, and identity, in check by routinely monitoring your bank balances, and reporting any suspicious or unauthorized transactions to your bank immediately.
Trusteer, the world’s leading provider of secure web access services, detected these schemes and says hotel poaching is a virile trade in underground and tech forums. Attack codes can be purchased in Visa underground forums for $280 and the spyware cannot be detected by anti-virus software. The package even includes a manual loaded with tips on how the poacher can trick the desk clerk into loading the spyware for them.
Malware writers often repackage their malicious installers with new algorithms in order to evade signature-based antivirus detection, said Bogdan Botezatu, a senior e-threat analyst at antivirus vendor BitDefender.
"The fact that the RAT's creator decided to target the hospitality industry is consistent with a recently observed change in the focus of cybercriminals - an expansion from online banking attacks to attacks against PoS systems, Criminals are increasingly expanding the focus of their attacks from online banking targets to enterprises," said Trusteer's CTO Amit Klein.
While this credit card scam seems nearly impossible to detect and prevent, you can keep your finances, and identity, in check by routinely monitoring your bank balances, and reporting any suspicious or unauthorized transactions to your bank immediately.
Cyber Attack on The Iranian Oil Ministry's Computer Network
The Iranian oil ministry's computer network came under attack from hackers and a computer virus, prompting the Islamic Republic to disconnect the country's main oil export terminal from the internet as a preventative measure, a semiofficial news agency reported on Monday.
The Mehr News Agency, which is a semi-official arm of the Iranian government, reported Monday that the country's principal oil terminal on Kharg Island was disconnected from the Internet as part of the response to the attacks. Email systems associated with the targets were also pulled offline.
Iranian officials said the virus attack, which began in earnest Sunday afternoon, had not affected oil production or exports, since the industry was still primarily mechanical and does not rely on the Internet. Officials said they were disconnecting the oil terminals and possibly some other installations in an effort to combat the virus.
Cyberattacks by well-resourced, highly capable and relentless, usually state-sponsored attackers so called advanced persistent threats are growing. The best known example is Stuxnet, which was aimed at Iran’s nuclear centrifuges and is widely believed to have been developed by the US or Israel, neither of which have confirmed their involvement.
The Iranian Students News Agency said that the virus, called “wiper” by its creator, had successfully erased information on hard disks at the Oil Ministry’s headquarters, a hulking black glass skyscraper on Taleghani Street in central Tehran.
Hamdullah Mohammadnejad, the head of civil defence at the oil ministry, was reported as saying Iranian authorities had set up a crisis unit and were working out how to neutralise the attacks.
The Mehr News Agency, which is a semi-official arm of the Iranian government, reported Monday that the country's principal oil terminal on Kharg Island was disconnected from the Internet as part of the response to the attacks. Email systems associated with the targets were also pulled offline.
Iranian officials said the virus attack, which began in earnest Sunday afternoon, had not affected oil production or exports, since the industry was still primarily mechanical and does not rely on the Internet. Officials said they were disconnecting the oil terminals and possibly some other installations in an effort to combat the virus.
Cyberattacks by well-resourced, highly capable and relentless, usually state-sponsored attackers so called advanced persistent threats are growing. The best known example is Stuxnet, which was aimed at Iran’s nuclear centrifuges and is widely believed to have been developed by the US or Israel, neither of which have confirmed their involvement.
The Iranian Students News Agency said that the virus, called “wiper” by its creator, had successfully erased information on hard disks at the Oil Ministry’s headquarters, a hulking black glass skyscraper on Taleghani Street in central Tehran.
Hamdullah Mohammadnejad, the head of civil defence at the oil ministry, was reported as saying Iranian authorities had set up a crisis unit and were working out how to neutralise the attacks.
Google raises Hackers bounties to $20,000
Google on Monday raised to $20,000 its bounty on software bugs that hackers could exploit for cyber attacks on the Internet giant's online services.
The maximum reward for exposing a vulnerability that would let an intruder's code get up to mischief in a Google data centre was ramped up from the $US3,133 ($A3,030) payout set when the bounty program was launched in November of 2010.
Remote code flaws found in Google's Web apps will also be rewarded $20,000.The term "remote code execution" refers to the most serious category of vulnerabilities, those which when exploited allow an attacker to hijack a system and/or plant malware on a machine.
A $10,000 bounty will be paid for SQL injection bugs or significant authentication bypass or data leak vulnerabilities, Google said in the revised rules for the program.
At Google’s Pwnium contest in March, Google paid out $60,000 prizes to anyone that could exploit the Chrome browser. Two people managed to do so, and collected the money. Even at that rate, security researchers have made it clear the exploits would have been worth more if sold to malicious individuals. Google’s $20,000 top payment is likely still far below the market rate.
The bounty was raised to inspire software savants to hunt for difficult-to-find, and potentially perilous, bugs hidden deep in programs
The maximum reward for exposing a vulnerability that would let an intruder's code get up to mischief in a Google data centre was ramped up from the $US3,133 ($A3,030) payout set when the bounty program was launched in November of 2010.
Remote code flaws found in Google's Web apps will also be rewarded $20,000.The term "remote code execution" refers to the most serious category of vulnerabilities, those which when exploited allow an attacker to hijack a system and/or plant malware on a machine.
A $10,000 bounty will be paid for SQL injection bugs or significant authentication bypass or data leak vulnerabilities, Google said in the revised rules for the program.
At Google’s Pwnium contest in March, Google paid out $60,000 prizes to anyone that could exploit the Chrome browser. Two people managed to do so, and collected the money. Even at that rate, security researchers have made it clear the exploits would have been worth more if sold to malicious individuals. Google’s $20,000 top payment is likely still far below the market rate.
The bounty was raised to inspire software savants to hunt for difficult-to-find, and potentially perilous, bugs hidden deep in programs
Saturday, April 14, 2012
Ultimate GPU Bruteforcer - Crack passwords with 450 Million passwords/Sec Speed
Extreme GPU Bruteforcer, developed by InsidePro is a program meant for the recovery of passwords from hashes of different types, utilizing the power of GPU which enables reaching truly extreme attack speed of approx 450 Millions passwords/Second .
The software supports hashes of the following types: MySQL, DES, MD4, MD5, MD5(Unix), MD5(phpBB3), MD5(Wordpress), NTLM, Domain Cached Credentials, SHA-1, SHA-256, SHA-384, SHA-512 and many others.
The software implements several unique attacks, including mask and hybrid dictionary attacks, which allow recovering even the strongest passwords incredibly fast. Utilizing the power of multiple graphics cards running simultaneously (supports up to 32 GPU), the software allows reaching incredible search speeds of billions of passwords per second!
Type hashes average speed (Using NVIDIA GTS250):
MD5 420 000 000 n / a
MySQL 1.08 billion n / a
MD4 605 000 000 n / a
NTLM 557 000 000 n / a
SHA-1 120 000 000 n / a
MySQL5 66 million p / s
LM 49 million p / s
The Program is easy to use, to launch the program, just pass the command-line parameters like - Name of the INI file with attack settings and Name of the text file with hashes.
INI File Parameters
[Settings]
AttackMode=1
LastPassword=
CurrentDevice=1
StreamProcessors=128
PasswordsPerThread=3000
Base64Hashes=0
AttackTime=0
DeleteHashes=0
OutputFileFormat=0
AppendToOutputFile=1
AppendToDictionaryFile=1
CustomCharacterSet1=
; ...
CustomCharacterSet9=
CustomCharacterSetA=
; ...
CustomCharacterSetZ=
[BruteForceAttack]
1=?d,0,9
2=?l?d,1,7
3=?l?d?s?u,1,5
[MaskAttack]
1=?u?l?l?l?l
[DictionaryAttack]
1=Dictionaries\InsidePro (Mini).dic
2=Dictionaries\PasswordsPro.dic
[HybridAttack]
Dictionary=Dictionaries\InsidePro (Mini).dic
1=@
2=@?d
3=@?d?d
The name of a text file with hashes. The format string to hash a "one line = one hash". In the distribution of the program includes test files with examples of hashes.
egb_ntlm+%281%29
The software supports hashes of the following types: MySQL, DES, MD4, MD5, MD5(Unix), MD5(phpBB3), MD5(Wordpress), NTLM, Domain Cached Credentials, SHA-1, SHA-256, SHA-384, SHA-512 and many others.
The software implements several unique attacks, including mask and hybrid dictionary attacks, which allow recovering even the strongest passwords incredibly fast. Utilizing the power of multiple graphics cards running simultaneously (supports up to 32 GPU), the software allows reaching incredible search speeds of billions of passwords per second!
Type hashes average speed (Using NVIDIA GTS250):
MD5 420 000 000 n / a
MySQL 1.08 billion n / a
MD4 605 000 000 n / a
NTLM 557 000 000 n / a
SHA-1 120 000 000 n / a
MySQL5 66 million p / s
LM 49 million p / s
The Program is easy to use, to launch the program, just pass the command-line parameters like - Name of the INI file with attack settings and Name of the text file with hashes.
INI File Parameters
[Settings]
AttackMode=1
LastPassword=
CurrentDevice=1
StreamProcessors=128
PasswordsPerThread=3000
Base64Hashes=0
AttackTime=0
DeleteHashes=0
OutputFileFormat=0
AppendToOutputFile=1
AppendToDictionaryFile=1
CustomCharacterSet1=
; ...
CustomCharacterSet9=
CustomCharacterSetA=
; ...
CustomCharacterSetZ=
[BruteForceAttack]
1=?d,0,9
2=?l?d,1,7
3=?l?d?s?u,1,5
[MaskAttack]
1=?u?l?l?l?l
[DictionaryAttack]
1=Dictionaries\InsidePro (Mini).dic
2=Dictionaries\PasswordsPro.dic
[HybridAttack]
Dictionary=Dictionaries\InsidePro (Mini).dic
1=@
2=@?d
3=@?d?d
The name of a text file with hashes. The format string to hash a "one line = one hash". In the distribution of the program includes test files with examples of hashes.
egb_ntlm+%281%29
- The name of a text file with hashes. The format string to hash a "one line = one hash". In the distribution of the program includes test files with examples of hashes.
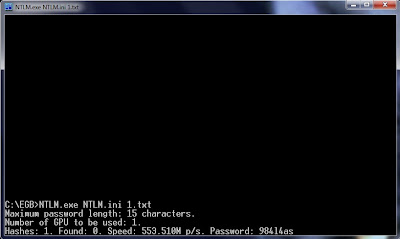
Here in above screenshot you can see that a alphanumeric 7 character NTLM password cracked with the speed of 553.510 Million passwords per second, this cracking process takes a few second to get the actual hash value by bruteforce process.
In another Example a 7 character alphanumeric MD5 password cracked with speed of 423.966 million passwords per second.
The main requirement is that your video card must support the CUDA technology. By default, the program is configured to run in the extreme operating mode to recovering passwords at the highest speed possible. But if it slow down your PC, then you can decrease the load on your computer, decrease the value in the PasswordsPerThread parameter in the INI file.
Download Trial or Buy Full Version here
In another Example a 7 character alphanumeric MD5 password cracked with speed of 423.966 million passwords per second.
The main requirement is that your video card must support the CUDA technology. By default, the program is configured to run in the extreme operating mode to recovering passwords at the highest speed possible. But if it slow down your PC, then you can decrease the load on your computer, decrease the value in the PasswordsPerThread parameter in the INI file.
Download Trial or Buy Full Version here
Hacks Against CISPA
Two technology trade associations said they were targeted by the hacker-activist group Anonymous as it singled out supporters of proposed legislation to improve U.S. cybersecurity.
The hacker group Anonymous claimed responsibility for taking down the websites of USTelecom and Tech America, which both back the Cyber Intelligence Sharing and Protection Act of 2011. Both sites remained unreachable as of Monday afternoon.
The attacks began yesterday when users were unable to log onto the sites. USTelecom represents telecom companies, including AT&T, Verizon, and CenturyLink; and TechAmerica's members include tech companies such as IBM, Microsoft, and Apple.
A Twitter account called @Anon_Central yesterday called the Rogers bill “draconian” and posted a link to groups and companies supporting the legislation.[ See List here ]
Anonymous posted a YouTube video showing USTelecom's site down Sunday, and the site was down for about 24 hours, according to a USTelecom spokesman.
Anonymous on Friday released a YouTube video threatening supporters of the Cyber Intelligence Sharing and Protection Act, a bill focused on encouraging U.S. government agencies and private businesses to trade information about cyberattacks.
The Cyber Intelligence Sharing and Protection Act of 2011 (CISPA), sponsored by Reps. Mike Rogers (R-Mich.) and Dutch Ruppersberger (D-Md.), has recently caught the attention of online activists, who are comparing it to the now-shelved Stop Online Piracy Act (SOPA).
Lawmakers say the goal of CISPA is to help companies beef up their defenses against hackers who steal business secrets, rob customer financial information and wreak havoc on computer systems. The bill would tear down legal barriers that discourage companies from sharing information about cyberattacks.
But privacy advocates warn the legislation could lead companies to share private user information with federal spy agencies. The House is expected to vote on the cybersecurity measure on the week of April 23.
The hacker group Anonymous claimed responsibility for taking down the websites of USTelecom and Tech America, which both back the Cyber Intelligence Sharing and Protection Act of 2011. Both sites remained unreachable as of Monday afternoon.
The attacks began yesterday when users were unable to log onto the sites. USTelecom represents telecom companies, including AT&T, Verizon, and CenturyLink; and TechAmerica's members include tech companies such as IBM, Microsoft, and Apple.
A Twitter account called @Anon_Central yesterday called the Rogers bill “draconian” and posted a link to groups and companies supporting the legislation.[ See List here ]
Anonymous posted a YouTube video showing USTelecom's site down Sunday, and the site was down for about 24 hours, according to a USTelecom spokesman.
Anonymous on Friday released a YouTube video threatening supporters of the Cyber Intelligence Sharing and Protection Act, a bill focused on encouraging U.S. government agencies and private businesses to trade information about cyberattacks.
The Cyber Intelligence Sharing and Protection Act of 2011 (CISPA), sponsored by Reps. Mike Rogers (R-Mich.) and Dutch Ruppersberger (D-Md.), has recently caught the attention of online activists, who are comparing it to the now-shelved Stop Online Piracy Act (SOPA).
Lawmakers say the goal of CISPA is to help companies beef up their defenses against hackers who steal business secrets, rob customer financial information and wreak havoc on computer systems. The bill would tear down legal barriers that discourage companies from sharing information about cyberattacks.
But privacy advocates warn the legislation could lead companies to share private user information with federal spy agencies. The House is expected to vote on the cybersecurity measure on the week of April 23.
A New Malicious Android application stealing banking credentials
A new form of smart Android malware can not only steal your online banking information, but update itself in the future and secretly send contact information stored on your device off to the Bad Guys. Security researchers at McAfee have discovered a malicious Android application capable of grabbing banking passwords from a mobile device without infecting the user’s computer.
From a McAfee blog post on the subject, penned by Malware Researcher Carlos Castillo: "To get the fake token, the user must enter the first factor of authentication (used to obtain initial access to the banking account). If this action is not performed, the application shows an error. When the user clicks “Generar” (Generate), the malware shows the fake token (which is in fact a random number) and sends the password to a specific cell phone number along with the device identifiers (IMEI and IMSI). The same information is also sent to one of the control servers along with further data such as the phone number of the device."
The app also includes a number of nasty lines of code that could be used to obtain users' contact lists and then send them off to a control server. "From man-in-the-middle attacks we now see more sophisticated, remote-controlled banking Trojans that can get more than one factor of authentication and update itself to, for example, modify a phishing attack to get other required credentials–such as the name or the ID number of the user–to perform electronic fraud," writes Castillo. "Due to the increasing popularity of Android and mobile-banking applications, we expect that more threats like this will appear."
If Mobile banking does take off, beware, since the Android security architecture won't be able to stop those types of attacks, given the ease with which users can be tricked, via social engineering attacks, into installing third-party applications.
From a McAfee blog post on the subject, penned by Malware Researcher Carlos Castillo: "To get the fake token, the user must enter the first factor of authentication (used to obtain initial access to the banking account). If this action is not performed, the application shows an error. When the user clicks “Generar” (Generate), the malware shows the fake token (which is in fact a random number) and sends the password to a specific cell phone number along with the device identifiers (IMEI and IMSI). The same information is also sent to one of the control servers along with further data such as the phone number of the device."
The app also includes a number of nasty lines of code that could be used to obtain users' contact lists and then send them off to a control server. "From man-in-the-middle attacks we now see more sophisticated, remote-controlled banking Trojans that can get more than one factor of authentication and update itself to, for example, modify a phishing attack to get other required credentials–such as the name or the ID number of the user–to perform electronic fraud," writes Castillo. "Due to the increasing popularity of Android and mobile-banking applications, we expect that more threats like this will appear."
If Mobile banking does take off, beware, since the Android security architecture won't be able to stop those types of attacks, given the ease with which users can be tricked, via social engineering attacks, into installing third-party applications.
TigerBot = SMS Controlled Android Malware Stealing Informations
A new form of Android malware controlled via SMS messages has been discovered and the malware can record phone calls, upload the device’s GPS location, and reboot the phone, among other things.
Researchers at NQ Mobile, working alongside researchers at North Carolina State University, have discovered this Android malware called "TigerBot", differs from “traditional” malware in that it is controlled via SMS rather than from a command & control (C&C) server on the Internet.
A common aspect of Android malware is the use of a command and control server that tells the malware what to do next and acts as a repository for any captured passwords or banking information.
The current information about this malware show that it can execute a range of commands including uploading the phone’s current location, sending SMS messages, and even recording phone calls. It works by intercepting SMS messages sent to the phone and checking to see if they are commands for it to act. If they are, it executes the command and then prevents the message from being seen by the user.
TigerBot tries to hide itself from the user by not showing any icon on the home screen and by using legitimate sounding app names (like System) or by copying names from trusted vendors like Google or Adobe.
Based on our current analysis, it supports the following commands:
Record the sounds in the phone, including the phone calls, the surrounding sounds and etc.
Change the network setting.
Upload the current GPS location.
Capture and upload the image.
Send SMS to a particular number.
Reboot the phone.
Kill other running processes.
To avoid becoming a victim, Only download applications from trusted sources, reputable application stores, and markets, and be sure to check reviews, ratings and developer information before downloading.
Researchers at NQ Mobile, working alongside researchers at North Carolina State University, have discovered this Android malware called "TigerBot", differs from “traditional” malware in that it is controlled via SMS rather than from a command & control (C&C) server on the Internet.
A common aspect of Android malware is the use of a command and control server that tells the malware what to do next and acts as a repository for any captured passwords or banking information.
The current information about this malware show that it can execute a range of commands including uploading the phone’s current location, sending SMS messages, and even recording phone calls. It works by intercepting SMS messages sent to the phone and checking to see if they are commands for it to act. If they are, it executes the command and then prevents the message from being seen by the user.
TigerBot tries to hide itself from the user by not showing any icon on the home screen and by using legitimate sounding app names (like System) or by copying names from trusted vendors like Google or Adobe.
Based on our current analysis, it supports the following commands:
Record the sounds in the phone, including the phone calls, the surrounding sounds and etc.
Change the network setting.
Upload the current GPS location.
Capture and upload the image.
Send SMS to a particular number.
Reboot the phone.
Kill other running processes.
To avoid becoming a victim, Only download applications from trusted sources, reputable application stores, and markets, and be sure to check reviews, ratings and developer information before downloading.
Hacker plans to take down Great Firewall of China
Anonymous plans to launch more attacks on Chinese government Web sites in an effort to highlight corruption and push for human rights improvements. While they managed to deface well over 500 sites we are now hearing they aren’t finished yet and have even more plans for the Chinese government coming soon, and bigger targets.
The group used the Twitter account “Anonymous China” to publicise the attacks, posting links to data files that contained passwords and other personal information from the hacked websites. This comes just days after all the attacks last week that even had messages warning of the downfall of the Chinese government.
The attacks are part of a bigger plan according to Anonymous hacker “f0ws3r” who told Reuters that the group is hoping to take down the “Great Firewall of China” A recent tweet from the Anonymous China Twitter feed confirms the group’s plans.
They claim to have hundreds of translators helping them hack Chinese Web sites. This is consistent with the hacks that happened a few weeks ago being displayed in English instead of Chinese.
The hacker declined to give further details on the next round of attacks, except to say it may hit bigger targets.The United States says it has suffered many high-profile hacking attacks that appear to come from China, often targeting human rights groups as well as U.S. companies. China maintains that it too is a victim of hacking attacks.
How Hackers can Track your Mobile phone
University of Minnesota researchers found a flaw in AT&T and T-Mobile cell towers that reveals the location of phone users. The attack, described in a Research paper (Click to Download Pdf), is most useful for determining whether a target is within a given geographic area as large as about 100 square kms or as small as one square kilometer. It can also be used to pinpoint a target's location but only when the attacker already knows the city, or part of a city, the person is in.
Ph.D. student Denis Foo Kune says, “Cell phone towers have to track cell phone subscribers to provide service efficiently. For example, an incoming voice call requires the network to locate that device so it can allocate the appropriate resources to handle the call. Your cell phone network has to at least loosely track your phone within large regions in order to make it easy to find it“.
The messages contain I.D. codes. In order to match the codes to the cell phone number, researchers called the phone three times. The code that appeared three times in the same time period in which researchers were listening in is most likely the code of the cell phone.“From there we can use that I.D. to determine if you’re around a certain area or if you’re on a particular cell tower,” he said.
The process requires a feature cellphone and a laptop, running the open-source Osmocom GSM firmware and software respectively, along with a cable connecting the two devices. It also uses a separate cellphone and landline.

The attackers use the landline to call the target's cellphone when it's located near the same LAC as the equipment and use the laptop output to monitor the broadcasts that immediately follow over the airwaves to page the target phone.
The attackers use the landline to call the target's cellphone when it's located near the same LAC as the equipment and use the laptop output to monitor the broadcasts that immediately follow over the airwaves to page the target phone.
The implications of this research highlight possible personal safety issues. The group explains their work in a recently presented at the 19th Annual Network & Distributed System Security Symposium and was titled “Location Leaks on the GSM Air Interface”. The group has also contacted AT&T and Nokia with some low-cost options that could be implemented without changing the hardware.
Your Facebook credentials at risk on Android
Facebook allows its authentication credentials to be stored in plain text within the Apple iOS version of its mobile app, allowing an attacker complete control over your Facebook account if he knows where to look.
Security researcher Gareth Wright noted the vulnerability and alerted Facebook. Wright wrote on his blog that he discovered the issue while exploring the application directories in his iPhone with a free tool and came across a Facebook access token in the Draw Something game on his phone.
The simple ‘hack’ allows a user to copy a plain text file off of the device and onto another one. This effectively gives another user access to your account, profile and all on that iOS device.
Facebook’s native apps for the two platforms not encrypting your login credentials, meaning they can be easily swiped over a USB connection, or more likely, via malicious apps. Facebook has responded that this issue only applies to compromised or jailbroken devices.
"My jaw dropped as over the next few minutes I watched posts appear on my wall, private messages sent, webpages liked and applications added," Wright wrote. Wright said that he harvested over 1,000 plists over the course of a week, although he copied no data.
As for the USB connection scenario, Facebook says there’s no way to fix this problem. Note that in this case it doesn’t matter if your device is jailbroken or not, because whoever is doing the deed has physical access to your phone or tablet.
Facebook said in a statement that the modifications made to the phone were responsible for exposing the data:
Facebook's iOS and Android applications are only intended for use with the manufacture provided operating system, and access tokens are only vulnerable if they have modified their mobile OS (i.e. jailbroken iOS or modded Android) or have granted a malicious actor access to the physical device. We develop and test our application on an unmodified version of mobile operating systems and rely on the native protections as a foundation for development, deployment and security, all of which is compromised on a jailbroken device. As Apple states, "unauthorized modification of iOS could allow hackers to steal personal information ... or introduce malware or viruses." To protect themselves we recommend all users abstain from modifying their mobile OS to prevent any application instability or security issues.
Wright called Facebook's statement "rubbish," adding that the vulnerability is present on both jailbroken and non-jailbroken phones.
Security researcher Gareth Wright noted the vulnerability and alerted Facebook. Wright wrote on his blog that he discovered the issue while exploring the application directories in his iPhone with a free tool and came across a Facebook access token in the Draw Something game on his phone.
The simple ‘hack’ allows a user to copy a plain text file off of the device and onto another one. This effectively gives another user access to your account, profile and all on that iOS device.
Facebook’s native apps for the two platforms not encrypting your login credentials, meaning they can be easily swiped over a USB connection, or more likely, via malicious apps. Facebook has responded that this issue only applies to compromised or jailbroken devices.
"My jaw dropped as over the next few minutes I watched posts appear on my wall, private messages sent, webpages liked and applications added," Wright wrote. Wright said that he harvested over 1,000 plists over the course of a week, although he copied no data.
As for the USB connection scenario, Facebook says there’s no way to fix this problem. Note that in this case it doesn’t matter if your device is jailbroken or not, because whoever is doing the deed has physical access to your phone or tablet.
Facebook said in a statement that the modifications made to the phone were responsible for exposing the data:
Facebook's iOS and Android applications are only intended for use with the manufacture provided operating system, and access tokens are only vulnerable if they have modified their mobile OS (i.e. jailbroken iOS or modded Android) or have granted a malicious actor access to the physical device. We develop and test our application on an unmodified version of mobile operating systems and rely on the native protections as a foundation for development, deployment and security, all of which is compromised on a jailbroken device. As Apple states, "unauthorized modification of iOS could allow hackers to steal personal information ... or introduce malware or viruses." To protect themselves we recommend all users abstain from modifying their mobile OS to prevent any application instability or security issues.
Wright called Facebook's statement "rubbish," adding that the vulnerability is present on both jailbroken and non-jailbroken phones.
Monday, April 9, 2012
More than 600000 Macs system infected with Flashback Botnet
The computer security industry is buzzing with warnings that more than half a million Macintosh computers may have been infected with a virus targeting Apple machines.
Dr. Web originally reported Wednesday that 550,000 Macintosh computers were infected by the growing Mac botnet. But later in the day, Dr. Web malware analyst Sorokin Ivan announced on Twitter that the number of Macs infected with Flashback had increased to 600,000, with 274 of those based in Cupertino, Calif.
Dr. Web explained that a system gets infected with the Mac Flashback trojan "after a user is redirected to a bogus site from a compromised resource or via a traffic distribution system." A specific JavaScript code on the site that contains the virus is then used to load a Java applet, which is how the malware makes its way onto a user's computer.
This Trojan spreads via infected web pages and exploits Java vulnerabilities that have been known for some time, yet Apple didn’t see fit to release a patch until this week (Java for Mac OS X 10.6 Update 7 and Java for OS X Lion 2012-001).
Macs have historically been an unappealing hacking target because of their low market share. Instead, criminals have attacked personal computers running Microsoft Corp.’s Windows software, seeking the biggest number of victims for illicit moneymaking schemes. Windows runs on more than 90 percent of the world’s desktop computers, according to market researcher Net Applications.
'All the stuff the bad guys have learnt for doing attacks in the PC world is now starting to transition to the Mac world,' McAfee Labs director of threat intelligence Dave Marcus told.
Once installed, the Flashback will inject code into Web browsers and other applications like Skype to harvest passwords and other information from those program's users.Security company F-Secure has published instructions on how to determine whether a Mac is infected with Flashback.
'There has been a significant increase in Mac malware in the last several quarters, so what we've seen with the Flashback Trojan isn't particularly surprising,' Marcus said.'Cybercriminals will attack any operating system with valuable information, and as the popularity of Macs increase, so will attacks on the Mac platform.'
Dr. Web originally reported Wednesday that 550,000 Macintosh computers were infected by the growing Mac botnet. But later in the day, Dr. Web malware analyst Sorokin Ivan announced on Twitter that the number of Macs infected with Flashback had increased to 600,000, with 274 of those based in Cupertino, Calif.
Dr. Web explained that a system gets infected with the Mac Flashback trojan "after a user is redirected to a bogus site from a compromised resource or via a traffic distribution system." A specific JavaScript code on the site that contains the virus is then used to load a Java applet, which is how the malware makes its way onto a user's computer.
This Trojan spreads via infected web pages and exploits Java vulnerabilities that have been known for some time, yet Apple didn’t see fit to release a patch until this week (Java for Mac OS X 10.6 Update 7 and Java for OS X Lion 2012-001).
Macs have historically been an unappealing hacking target because of their low market share. Instead, criminals have attacked personal computers running Microsoft Corp.’s Windows software, seeking the biggest number of victims for illicit moneymaking schemes. Windows runs on more than 90 percent of the world’s desktop computers, according to market researcher Net Applications.
'All the stuff the bad guys have learnt for doing attacks in the PC world is now starting to transition to the Mac world,' McAfee Labs director of threat intelligence Dave Marcus told.
Once installed, the Flashback will inject code into Web browsers and other applications like Skype to harvest passwords and other information from those program's users.Security company F-Secure has published instructions on how to determine whether a Mac is infected with Flashback.
'There has been a significant increase in Mac malware in the last several quarters, so what we've seen with the Flashback Trojan isn't particularly surprising,' Marcus said.'Cybercriminals will attack any operating system with valuable information, and as the popularity of Macs increase, so will attacks on the Mac platform.'
Internet Censorship : CISPA - Newest Cyber Security Bill
If you download and distribute copyrighted material on the Internet, or share any information that governments or corporations find inconvenient, you could soon be labeled a threat to national security in the United States. That’s the aim of a bill in Congress called the Cyber Intelligence Sharing and Protection Act (CISPA).
The good news is that SOPA and PIPA haven’t come to pass, but the bad news is that they could be followed by a bill that is even more invasive and could violate even more of your civil liberties. According to a press release issued last week, the bill already has over a 100 congressional co-sponsors. Yet the bill is only now beginning to appear on the public radar.
CISPA would let companies spy on users and share private information with the federal government and other companies with near-total immunity from civil and criminal liability. It effectively creates a ‘cybersecurity’ exemption to all existing laws.
CISPA, however, is nothing like SOPA, despite its recent association in the media. While SOPA included provisions that would have essentially broken the Internet by allowing the U.S. to delete domains from a central registry system, CISPA does nothing of the sort, and aims more at “cyber threat intelligence” gathering than censorship and piracy prevention.
The bill presents itself as a simple enhancement of America’s cyber-security that would amend the National Security Act to include “cyber threat intelligence” gathering. To those ends, it would tear down the firewall between private corporate networks and the National Security Agency , enabling corporations to share data with the world’s most sophisticated spy apparatus.
While the bill is openly supported by companies like AT&T, Lockheed Martin, Microsoft, Facebook, Boeing and Intel, ACLU legislative counsel Michelle Richardson cautioned last month that it is not something to be taken up lightly.
The good news is that SOPA and PIPA haven’t come to pass, but the bad news is that they could be followed by a bill that is even more invasive and could violate even more of your civil liberties. According to a press release issued last week, the bill already has over a 100 congressional co-sponsors. Yet the bill is only now beginning to appear on the public radar.
CISPA would let companies spy on users and share private information with the federal government and other companies with near-total immunity from civil and criminal liability. It effectively creates a ‘cybersecurity’ exemption to all existing laws.
CISPA, however, is nothing like SOPA, despite its recent association in the media. While SOPA included provisions that would have essentially broken the Internet by allowing the U.S. to delete domains from a central registry system, CISPA does nothing of the sort, and aims more at “cyber threat intelligence” gathering than censorship and piracy prevention.
The bill presents itself as a simple enhancement of America’s cyber-security that would amend the National Security Act to include “cyber threat intelligence” gathering. To those ends, it would tear down the firewall between private corporate networks and the National Security Agency , enabling corporations to share data with the world’s most sophisticated spy apparatus.
While the bill is openly supported by companies like AT&T, Lockheed Martin, Microsoft, Facebook, Boeing and Intel, ACLU legislative counsel Michelle Richardson cautioned last month that it is not something to be taken up lightly.
Friday, April 6, 2012
" Facebook Dislike Button " Is A New Kind Of Spam
All of us use facebook and want a dislike button too for disliking some posts on facebook. Scammers are now using this need as their spam spreading method on facebook. Facebook scammers are tricking users to paste rogue code into their browser's address bars in order to get a Dislike button added to their options. The spam messages posted by victims read "Facebook now has a dislike button! Click Enable Dislike Button' to turn on the new feature!" The scammers replace share link by a message "Enable Dislike Button".
After clicking the link, this message will share this spam message to all friends of user and also rune some rouge code on his system too.
Facebook has not announced any official dislike button and i do not think it will be in near future.
faceook security experts are doing their best for preventing spams on facebook, but spams are increasing day by day. I hope people will understand it's danger and use safe facebook. I advice users not to click on any this kind of spams and always enalbe all security features given by facebook
After clicking the link, this message will share this spam message to all friends of user and also rune some rouge code on his system too.
Facebook has not announced any official dislike button and i do not think it will be in near future.
faceook security experts are doing their best for preventing spams on facebook, but spams are increasing day by day. I hope people will understand it's danger and use safe facebook. I advice users not to click on any this kind of spams and always enalbe all security features given by facebook
Wednesday, April 4, 2012
Chinese hacker targeting indian government and tibetan activists sites
Websites of Indian government and Tibetan activists in the country are under attack in a cyber attack campaign engineered by a Chinese hacker, working with one of the world's largest e-tailers Tencent.
The cyber criminal in question is Gu Kaiyuan, once a graduate student at a Chinese university that receives government financial support for its computer security program and currently an employee at Chinese portal Tencent. Before Kaiyuan initiated the exploits, collectively called the Luckycat campaign, he was involved in recruiting students for his school’s computer security and defense research.
The Luckycat cyber campaign, has been linked to 90 attacks in recent past against targets in India and Japan, as well as against Tibetan activists, said the report released by the Japanese network security firm. 'Luckycat' has been able to compromise about 233 computers many of which are in India. A report on the campaign from cloud security company Trend Micro shows that the Luckycat perpetrators began around June 2011.
Also, Trend Micro was able to find a set of campaign codes used to monitor compromised systems. “The campaign codes often contain dates that indicate when each malware attack was launched. This demonstrates how actively and frequently the attackers launched attacks,” the report reads. “The campaign codes also reveal the attackers’ intent, as some of these referenced the intended targets.”
The report did not directly implicate the Chinese government, but security researchers believed that the style of the attacks and the types of targets indicated state-sponsored spying.
The cyber criminal in question is Gu Kaiyuan, once a graduate student at a Chinese university that receives government financial support for its computer security program and currently an employee at Chinese portal Tencent. Before Kaiyuan initiated the exploits, collectively called the Luckycat campaign, he was involved in recruiting students for his school’s computer security and defense research.
The Luckycat cyber campaign, has been linked to 90 attacks in recent past against targets in India and Japan, as well as against Tibetan activists, said the report released by the Japanese network security firm. 'Luckycat' has been able to compromise about 233 computers many of which are in India. A report on the campaign from cloud security company Trend Micro shows that the Luckycat perpetrators began around June 2011.
Also, Trend Micro was able to find a set of campaign codes used to monitor compromised systems. “The campaign codes often contain dates that indicate when each malware attack was launched. This demonstrates how actively and frequently the attackers launched attacks,” the report reads. “The campaign codes also reveal the attackers’ intent, as some of these referenced the intended targets.”
The report did not directly implicate the Chinese government, but security researchers believed that the style of the attacks and the types of targets indicated state-sponsored spying.
Subscribe to:
Posts (Atom)