Saturday, June 22, 2013
Thursday, June 20, 2013
Team Fortress 2 Skin - Blitz Pack
This is a cool new skin pack for Team Fortress 2 that will add black stripes under the eyes to each class in the game.
If you feel like changing some of the default skins in Team Fortress 2 you can try this new skin pack.
Requirements:
· Team Fortress 2
GTA IV Addon - AH-64D Longbow Apache
Gamers in search for some new and fun change of scenery for within the world of Grand Theft Auto IV, you can try out the new AH-64D Longbow Apache mod.
After unpacking the archive, you must copy the content in the following path: Rockstar Games/GTA IV/Models.
Requirements:
· Grand Theft Auto IV
GTA IV Addon - AH-64D Longbow Apache Israel
Those of you who are in search for some new and fun change of scenery for within the world of Grand Theft Auto IV, you can try out the new AH-64D Longbow Apache Israel mod.
After unpacking the archive, you must copy the content in the following path: Rockstar Games/GTA IV/Models.
Requirements:
· Grand Theft Auto IV
Small Fun Farkle 1.3.4
Small Fun Farkle is an addictive, easy to learn dice game for 1 to 8 players (human and/or customizable computer players) similar to the popular dice games "Ten Thousand" and "Press Your Luck." The separated, realistic score pad keeps the user interface uncluttered. Names in italics on the score pad indicate computer players and so on....
The game supports from one to eight players - any of which can be human or customizable computer opponents (Normal, Cautious, Fearless, Simple, or Random, Genius, or Moron). You can even set up an all computer match (don't worry, the computer won't blow up like in the movie "War Games"). If you have a favourite game setup, you can save it as the default.
Players can control the look and feel of the game by selecting the background pictures, dice styles, and sounds. You can even add your own backgrounds! Also available are some other options that help beginners learn to play and make game play easier for more experienced players.
If you get an impressive single-round score your name may be immortalized by being added to the High Rollers list. For additional bragging rights, if you finish far ahead of the other players your name can be added to the Biggest Whoopin' (Highest Margin of Victory) list.
A hard-earned victory should be rewarded. So when you've left your opponents behind in the dust you'll be given the prestigious Small Fun Farkle Cup. Don't forget to thank all of the little people in your acceptance speech.
Requirements:
· OS: Win XP
Limitations:
· 10 days trial period
What's New in This Release: [ read full changelog ]
· Added 1 new set of dice and fixed an issue that may have inconvenienced some players.
Facebook Dislike 3.2
Facebook Dislike is a Firefox extension that adds a "Dislike" feature on Facebook.
"How to" YouTube Video :
http://www.youtube.com/watch?v=UAM_PdS4vaY
Facebook fan page :
http://www.facebook.com/pages/FBDislike/186845260403
Send Translation in your language here :
http://www.facebook.com/pages/FBDislike/186845260403
FBD is an add-on program for Facebook. FBD is a freeware and can be used without any restriction in personal environment. DOWEB is not affiliated with Facebook in any way. FBD adds the feature “dislike” to Facebook page and may disrupt the normal use of Facebook. If you notice any problem while using FBD along with Facebook, uninstall FBD before contacting Facebook’s customer support.
You may uninstall FBD at any time and with no limitations, using the standard uninstall procedures as offered with your Internet Browser
FBD is a free software but DOWEB may at any time adds advertisements in your Facebook page. The plugin does not launch pop-up or pop-under advertisement windows or any other type of obtrusive ads.
Product's homepage
Requirements:
· Mozilla Firefox
What's New in This Release: [ read full changelog ]
· Fix disliking comment bug
eHour 1.2.1
eHour is an open source webbased time tracking tool for consultancy companies and other project based businesses. eHour's primary objective is to keep time tracking as simple and user friendly as possible while still being very effective at measuring and reporting the amount of time your team spends on a project.
Product's homepage
Here are some key features of "eHour":
· create multiple projects per customer
· assign employees to projects
· have different start and end dates and hourly rates per employee to project assignment
· create default projects to which all employees should be assigned (days off, sick leave, etc.) so you can keep track of those hours as well
· turnover & booked hours reports on all customers, projects, employees, departments or a selection of them
· configure whether you want your employees see their turnover
· seperation of consultant, reporting and administration role.
What's New in This Release: [ read full changelog ]
· The underlying web framework (Wicket) has been upgraded from version 1.4.20 to 6.7.
· This fixes deployment issues on the latest Tomcat versions and increases browser compatibility.
· The export month feature was a bit enhanced.
· Instead of just exporting a month, you can now export any date range, be it a week or multiple months.
· The calendar/datepicker now uses the proper date format, and a Finnish translation is added.
· Many bugfixes have been made.
Gnome Control Center 3.8.3 / 3.9.3
Gnome Control Center is GNOME's main interface for configuration of various aspects of your desktop.
It is an open source Control Panel for the GNOME desktop environment.
Product's homepage
Requirements:
· GNOME
What's New in This Release: [ read full changelog ]
Bluetooth:
· Port to BlueZ 5
Background:
· show explanation of why pictures source might be empty
Power:
· Update UI strings to follow the HIG
All:
· Make a number of dialogues non-resizable
Region, Wacom, Shell:
· Set button arrow icons according to locale's text direction
Sound, Background:
· ensure dialogs are closed if panel changed
Shell:
· Raise the existing window when already opened
· Go back to overview when setting panel to NULL
Mouse:
· Rename "Content sticks to fingers" to "Natural Scrolling"
Sharing:
· retrieve the mDNS hostname from Avahi, if available
Region:
· Make sure not to display an empty input sources list
User Accounts:
· Don't let user disable own account
· Don't show heading for other accounts if there are none
· Hide 'Add Account' dialog when panel goes away
· After the add account dialog is cancelled, discard results
· Remove autologin when an account is deleted
· avoid problems with automatic login and disabled accounts
· prevent the only Administrator from being demoted
· prevent the only admin from being deleted or disabled
· User friendly password hints
· "Add user account" and password dialogs redesign
· Set the password mode to regular immediately
· Fix possible crashes when changing the language in the region panel if done after the user panel was opened
Wacom:
· Add command line argument support for choosing the tablet
· Add command line support for calibration
· Fix discrepancy when switching monitors from g-c-c
KeyBox 1.08.20
KeyBox is an open source and web-based application that provides an easy way to manage OpenSSH public keys, version 2.
KeyBox is also able to start a web-based SSH terminal, in order to execute scripts and commands on multiple SSH sessions, simultaneously.
After installation, KeyBox can be used by opening your web browser to http://localhost:8090. Login with:
username:admin
password:changeme
Product's homepage
Requirements:
· Java SE Development Kit
· SQLite
· Maven 2
· OpenSSH
What's New in This Release: [ read full changelog ]
· This release adds fixes the script dialog and changes how terminals are selected in the composite view.
Facebook for Linux
As its name suggests, Facebook for Linux is a free graphical application designed to act as a mobile Facebook App on your Linux desktop.
Facebook for Linux looks and acts exactly the same like the Facebook apps on an iPhone or Android smartphone.
Product's homepage
Show My IP Address 0.1
Show My IP Address is a simple Firefox extension that displays your public IP address in the Add-On bar.
Show My IP Address is an open source add-on designed to work with Mozilla Firefox 19.0 and later. This add-on does not require a browser restart.
Product's homepage
Requirements:
· Mozilla Firefox
Best Price by ShopVibe 2.11
Best Price by ShopVibe is a Firefox extension that enables users to get price comparisons and latest deals for many products, from numerous shopping sites.
Best Price by ShopVibe is an add-on designed to work with Mozilla Firefox 16.0 and later.
This add-on doesn't require you to restart the web browser.
Product's homepage
Requirements:
· Mozilla Firefox
Newssitter 2.3.0
Newssitter is a news reader for the Firefox sidebar for premium news feeds and your personal social media news.
The number of supported providers is growing daily: Facebook, New York Times, Guardian, Mashable, Tech Crunch, Technorati, Gizmodo, News York Observer,....
The news are displayed with images in a twitter like style. New news are shown as soon as the news are available by the news providers (news-ticker).
News recommendations from your personal news providers are shown in the news ticker, when you open an new page in the browser.
You can add new news providers very simple by clicking on the provider icon in the news-library or you can news feeds to Newssitter directly in the firefox feed-view.
News can be filtered by clicking on one or more provider icons in the vertical toolbar.
Your local news database will be fill with fresh news in the background, when they are available.
Product's homepage
Requirements:
· Mozilla Firefox
What's New in This Release: [ read full changelog ]
· Smaller news popup design
· Tag cloud with cardinality
· Image filter for twitter logos etc.
· Favicons used als icon for new feeds
Hammer Penguins 1.0.7
Small Fun Games has released Hammer Penguins, a new Windows tile-matching game for children and adults. Similar to the Mahjonng Solitaire genre of computer games, Hammer Penguins lets you help two penguins save their animal friends who have been trapped in the ice.
At the easiest levels, children of all ages will be able to pair matching tiles and release the trapped cows, puppies, and dozens of other animals from the ice. Parents can use the middle levels to play Hammer Penguins with their children, and teach them the principles of logic, strategy, and planning ahead. And a game at the high difficulty level will provide ten or twenty minutes of fun for even the most savvy gamer.
Each game board is a randomly shuffled set of 140 animal tiles that you need to match, two by two, until the entire board is cleared. The theory that determines the matching rules is simple and intuitive. But the game can be extremely challenging and complex. Hammer Penguins' infinite variety of game boards will keep you looking forward to the next game.
Players can enjoy a relaxed, untimed game or the more difficult set of Challenge Games. The Hint button will reveal one move that is available immediately, even though it might not be the best strategic move to help you clear the entire board. You can even toggle the sound off if you prefer to play a quiet game.
Whether you're a home computer user who wants to spend hours of relaxing fun playing a thoughtful, non-violent game, a businessperson who needs a way to take a challenging work break to relax and unwind, or a parent who wants to teach your kids to think logically and plan ahead, Hammer Penguins can provide years of entertainment.
Requirements:
· OS: Windows XP/Vista/7
Limitations:
· 5 Launches
What's New in This Release: [ read full changelog ]
· Brand new tutorial that auto-starts when the player hits "Play" for the first time
· Critter placement is improved. Looks a bit better and clicks should be more reliable.
· Animated text to give feedback when earning a time penalty from hints
TraficTube rev24
TraficTube is a Firefox extension that adds a button on the Add-On bar, implementing an extra style for the trafictube.ro website, expanding it to 100%.
TraficTube is an open source add-on designed to work with Mozilla Firefox 19.0 and later. This add-on does not require a browser restart.
Product's homepage
Requirements:
· Mozilla Firefox
CorneliOS 3.6r18
CorneliOS is a web based virtual operating system running on top of a host system (any BSD/UNIX system should fit).
CorneliOS offers services via HTML and/or XHTML over the web, which means that you can use it within any web browser without having to install any software on your local computer.
Product's homepage
What's New in This Release: [ read full changelog ]
· various CIOS Edu API UI enhancements
· new CorneliOS DBMS e-mail collection tool
· new CorneliOS navigation element styles
· improved CornelioSCRIPT nav command
· updated system images, language kits and style sheets
Gnome Icon Theme Symbolic 3.8.3
Gnome Icon Theme Symbolic's purpose is to extend the base icon theme that follows the Tango style guidelines for specific purposes.
This would include OSD messages, panel system/notification area, and possibly menu icons.
Icons follow the naming specification, but have a -symbolic suffix, so only applications specifically looking up these symbolic icons will render them. If a -symbolic icon is missing, the app will fall back to the regular name.
Product's homepage
Requirements:
· GNOME
What's New in This Release: [ read full changelog ]
· repeat-signle
· sync with gnome-icon-theme for notifications
· make status icons more legible (bug #698700)
· muted (bug #698700)
· window control icons (bug #697930)
· screen rotation status (bug #698257)
· headset vs headphones icon
Evince 3.8.2 / 3.9.3
Evince is an open source document viewer for the GNOME desktop environment.
Evince's goal is to replace the multiple document viewers that exist on the GNOME Desktop, like gpdf, ggv, and xpdf with a single simple application.
Product's homepage
Here are some key features of "Evince":
Supported formats:
· · PDF
· · Postscript
· · DJVU
· · DVI
· · Multipage tiff
Plans to include:
· · Comic book (*.cbr)
· · Powerpoint presentations
· · OO Impress presentations
What's New in This Release: [ read full changelog ]
New features and improvements:
· Make the history behave more like a web browser (Christian Persch)
· Add a fallback implementation of text selection for backends that implement get_selection_region but not render_selection (#669022, Jason Crain)
· Initial implementation of caret navigation added to libview (#638905, #702076, #702068, Antia Puentes, Carlos Garcia Campos)
· Add a GSetting to set a custom page cache size (#642683, Jonas Danielsson)
Bug fixes:
· Fix memory corruption in EvHistory implementation (#697397, Christian Persch)
· Fix drag and drop of selected text after zooming with a selection (#702406, Jason Crain)
· Fix a crash when searching with a negative current page (#683172, Germán Poo-Caamaño)
· Fix race condition in sidebar-thumbnails (#701900, aakash)
· Use horzontal/vertical GtkBoxes instead of deprecated GtkHBox/GtkVBox (Christian Persch)
· Fix runtime critical warning for links with NULL action (Christian Persch)
· Fix -Wstrict-prototypes warnings (Christian Persch)
· Remove obsolete g_type_init calls (Christian Persch)
· Fix crash on corrupted PDF with no pages (#701302, Germán Poo-Caamaño)
Translation updates:
· Marek ÄŒernocký (cs)
· Daniel Mustieles (es)
· Fran Dieguez (gl)
· OKANO Takayoshi (ja)
· Yasumichi Akahoshi (ja)
GTA IV Addon - AH-64D Longbow Apache United Kingdom
If you're ever in search for some new and fun change of scenery for within the world of Grand Theft Auto IV, you can try out the new AH-64D Longbow Apache United Kingdom mod.
After unpacking the archive, you must copy the content in the following path: Rockstar Games/GTA IV/Models.
Requirements:
· Grand Theft Auto IV
pgBadger 3.4
pgBadger is an open source software designed to analyze PostgreSQL database logs faster than any other existing tool.
pgBadger features detailed reports about SQL queries, including overall statistics, the slowest queries, queries that took up the most time, the most frequent queries, the most frequent errors.
pgBadger also provides hourly queries statistics, hourly temporary file statistics., hourly checkpoints statistics, locks statistics, and much more.
Product's homepage
Requirements:
· Perl
What's New in This Release: [ read full changelog ]
· This version added many graphical improvements and improved rendering of logs over a few hours.
· Bugs were fixed, especially in reports of queries that generate the most temporary files.
SabreDAV 1.8.5
SabreDAV is an open source software that allows you to easily add WebDAV support to a PHP application.
It is designed to cover the entire standard, and attempts to allow integration using an easy to understand API.
Product's homepage
Here are some key features of "SabreDAV":
· Fully WebDAV compliant
· Supports Windows XP, Windows Vista, Mac OS/X, DavFSv2, Cadaver, Netdrive, Open Office, and probably more.
· Passing all Litmus tests
· Supporting class 1, 2 and 3 webdav servers
· Locking support
· Custom property support
· Supports: RFC2518 and revisions from RFC4918
· Has built-in support for (basic/digest) authentication (RFC2617)
What's New in This Release: [ read full changelog ]
· The zip release ships with sabre/vobject 2.1.0.
· Sabre\DAV\Client::verifyPeer is now a protected property (instead of private).
· A problem where text was incorrectly escaped in the Href and HrefList properties, disallowing URLs with ampersands (&) in them was fixed.
· A deserializer was added for Sabre\DAVACL\Property\CurrentUserPrivilegeSet.
· An issue where the client only deserialized properties with status 200 was fixed.
· Escaping of XML in 423 Locked error responses was fixed.
· A beforeGetPropertiesForPath event was added.
Flash Video Downloader - Youtube Downloader 3.8.8
Flash Video Downloader - Youtube Downloader is a Firefox extension that adds a button on the Add-On bar and one on the navigation bar, as well as a download button on the YouTube video page, allowing users to effortlessly download videos from the YouTube website.
It allows user to download YouTube videos in various popular formats, such as MP4, 3GP, FLV or WebM, in both HD and SD resolutions.
Flash Video Downloader - Youtube Downloader is an open source add-on designed to work with Mozilla Firefox 3.0 or later and Firefox for Android 11.0 Alpha 1 - 17.0 Alpha 1.
Product's homepage
Requirements:
· Mozilla Firefox
What's New in This Release: [ read full changelog ]
· Fixed Mobile version
Torchlight II +22 Trainer for 1.9.5.1 - 1.22.5.40
This is an interesting trainer that will bring you: infinite health, infinite mana, infinite gold, infinite experience, infinite flame, infinite stat points, infinite skill points, add fame, add experience, add skill level max, 2x/4x/8x/16x gold, 2x/4x/8x/16x experience and other cool things.
NOTE: This trainer is for the 1.9.5.1 - 1.22.5.40 version of the game.
Horde Application Framework 5.1.1
Horde Application Framework is an open source software that provides the common tools a Web application requires.
Horde Application Framework is written in PHP and provides classes for dealing with compression, preferences, connection tracking, browser detection, MIME, and much more.
Product's homepage
What's New in This Release: [ read full changelog ]
· This version was updated for the new Twitter API.
· The Dutch, Japanese, and Spanish translations were updated.
Search in Google Scholar 1.0
Search in Google Scholar is a Firefox extension that extends your right-click context menu with the ability to search selected text or links from web pages in Google Scholar.
Search in Google Scholar is an open source add-on designed to work with Mozilla Firefox 3.6 and later. All searches will be opened in a new tab.
Product's homepage
Requirements:
· Mozilla Firefox
Zaqwes Tab Searcher 0.4
Zaqwes Tab Searcher is a Firefox extension that adds a button on the Add-On bar, allowing users to search content in all opened tabs.
Zaqwes Tab Searcher is an open source add-on designed to work with Mozilla Firefox 19.0 and later. This add-on does not require a browser restart.
Product's homepage
Requirements:
· Mozilla Firefox
What's New in This Release: [ read full changelog ]
· Bug fix.
Tumblr Savior 0.4.8
Tumblr Savior is a Firefox extension that adds a button on the Add-On bar, allowing users to easily blacklist or whitelist Tumblr terms.
Tumblr Savior is an open source add-on designed to work with Mozilla Firefox 6.0 and later. This add-on does not require a browser restart.
Product's homepage
Requirements:
· Mozilla Firefox
What's New in This Release: [ read full changelog ]
· It works with the current Tumblr Dashboard.
synctool 5.3
synctool is an administrative tool for working with clusters of computers.
synctool copies configuration files to groups of machines in your cluster based on what groups (or classes) they are in. By doing so, it keeps the configuration on that group of machines synchronized (or, "in sync").
If needed, synctool will restart or reload any daemons, as you wish. synctool can be easily extended to do other administrative tasks, such as checking daemons, checking free disk space, installing packages, etc. or any other task you want it to do.
synctool was developed by Walter de Jong from 2003 to 2006.
synctool simplyfies system administration by working with the following concepts:
· a host can be part of one or more groups, or classes
· files are designated a class by means of filename extension
· the 'overlay' directory tree contains the files and directories that should be copied (or 'synced') to the target host
· when certain files are updated, you will want to execute a script (eg, /etc/init.d/daemon restart)
· simplicity. It uses the power of rsync and ssh to distribute the files.
· extendibility. Make synctool more powerful by writing plugin scripts.
Installation:
· copy the contents of the bin/ directory to your local software directory, like /usr/local/bin/
These executables should be available on every node in your cluster. It is easy to use a shared filesystem for this, or use rcp, scp, rsync, or whatever file distribution mechanism you already have.
· setup a synctool repository on the master node:
mkdir /var/lib/synctool
· usually the masterdir is only accessible by root:
chown root.root /var/lib/synctool
chmod 700 /var/lib/synctool
· setup initial synctool repository directories:
mkdir /var/lib/synctool/overlay
mkdir /var/lib/synctool/delete
mkdir /var/lib/synctool/tasks
mkdir /var/lib/synctool/scripts
· edit the configuration file
cp synctool.conf.example /var/lib/synctool/synctool.conf
vi /var/lib/synctool/synctool.conf
· edit the .sh scripts to contain the correct path names
vi /usr/local/bin/synctool-local.sh
vi /usr/local/bin/synctool.sh
You should decide whether or not you want to administrate your master node with synctool as well. This is a personal preference; sometimes it is easier to apply synctool to the master node as well, sometimes it is wiser not to. The hosts that are under synctool's control are listed in synctool.conf, so if you want to exclude it, leave it out of the config file.
As stated in the README, the synctool python program does not do any network communication (like, for example, cfengine does). This means you have to synchronize the repository to all nodes in the cluster by other means; rsync is perfectly suited to do this job. It is also possible to put the synctool repository on a shared filesystem. This is not recommended for large clusters for performance reasons. By default, synctool is deployed together with a wrapper script synctool.sh
that does the following:
* rsync the repository to all nodes
* run synctool on all nodes via ssh
synctool uses rsync with ssh to copy files to all nodes. This means you will need to set up ssh with passwordless login for root from the masternode to the cluster nodes. This has some security implications. Be sure you understand every security aspect before bluntly opening up the nodes. See the SSH documentation (for OpenSSH, see http://www.openssh.org ) on possible ways to achieve this.
For sites with extra tight security, it is possible to configure ssh to run only specific (synctool) commands, or maybe you want to adapt the synctool.sh wrapper script so that it suits your security needs.
Product's homepage
Requirements:
· Python
· rsync
What's New in This Release: [ read full changelog ]
· This version fixed a number of small issues and notably two larger ones: the PATH environment variable is now searched for the configured commands.
· This helps on multi-platform setups.
· The --erased-saved option now is an action by itself.
· Using --erased-saved will no longer trigger other updates to occur inadvertently.
GTA IV Addon - AH-64D Longbow Apache Netherlands
Whenever you are in search for some new and fun change of scenery for within the world of Grand Theft Auto IV, you can try out the new Clockwork Mount mod.
After unpacking the archive, you must copy the content in the following path: Rockstar Games/GTA IV/Models.
Requirements:
· Grand Theft Auto IV
Group-Office 4.2.2
Group-Office is an office suite software, web-based and extensible by modules.
Group-Office comes with some interesting features, such as an email client, user management, a file manager, a project management, module management, a calendar, customer relations management and website management.
Group-Office allows you to sync your documents with Outlook and PDAs.
Product's homepage
Here are some key features of "Group-Office":
Speed:
· The World Wide Wait bugs us all every day and the critical business applications that Group-Office provides can't be hindered by being slow. Group-Office is specifically designed to perform tasks as quickly as possible.
Simplicity:
· The Graphical User Interface is designed in a way that everybody intuitively finds the functions they are looking for. Group-Office strives to be as simple as possible without losing functionality.
Modularity:
· As an ever-changing software product, upgrades should be as painless as possible. This means that good code design is critical. Group-Office is designed in a modular way that makes upgrades easy and painless.
Scalability:
· Group-Office is designed to be usable for 1 to thousands of user.
What's New in This Release: [ read full changelog ]
· Speed optimizations and new features for the ticket system and e-mail client. Upgrading is recommended.
BugHotel Reservation System 5.5.443
BugHotel Reservation System project is a hotel booking and accounting software package which uses the Internet to "network" your corporate office to each of your hotels.
All data processing occurs at the Application Service Provider (ASP) data center. Income statements, reports, etc. may be customized.
Product's homepage
Here are some key features of "BugHotel Reservation System":
· Improve Customer Satisfaction
· Reduce Your Costs
· Boost Your Sales
What's New in This Release: [ read full changelog ]
· This version added Discount Fee to View Reservations, View Requests, View Group Reservation, and View Group Reservations (Details).
· The Portuguese localization has been updated.
tinyurl to clipboard 0.1
tinyurl to clipboard is an open source add-on designed to work with Mozilla Firefox 19.0 and later. This add-on does not require a browser restart.
Product's homepage
Requirements:
· Mozilla Firefox
View the original article here
Team Fortress 2 Skin - I C SPY
If you are searching for a cool new Spy class skin for the world of Team Fortress 2 you can try the latest I C SPY skin pack.
Requirements:
· Team Fortress 2
View the original article here
Close other tabs 2.8
Close other tabs is a Firefox extension that adds the following three keyboard shortcuts to Firefox:
- Ctrl+Shift+F3 closes all tabs on the left of the active one
- Ctrl+Shift+F4 closes all tabs except the active one
- Ctrl+Shift+F5 closes all tabs on the right of the active one
Product's homepage
Requirements:
· Mozilla Firefox
What's New in This Release: [ read full changelog ]
· Bugfix: migration vom deprecated interface nsIDOMWindowInternal to nsIDOMWindow.
Blue Smiley Organizer 5.52
Blue Smiley Organizer is Web-based script to manage your bookmarks, diary, reminders, to-do lists, contacts, knowledge, and images in a multi-user environment.
Blue Smiley Organizer also includes its own live support help system, blogs, themes, and a discussion forum.
Product's homepage
Here are some key features of "Blue Smiley Organizer":
· Prioritize your bookmarks: Tell BlueSmiley how important a website is to you and how often you want to visit the link (e.g. once a month) and a list of bookmarks will be generated with the most urgent bookmarks at the top of the list.
· You can also keep a diary, manage your To-Do List and save email addresses and telephone numbers with the Contact Management. Add important vocabulary, snippets of code, etc to the categorized knowledge list.
· BlueSmiley reminds you of birthdays, TV shows, appointments, etc.
· Want to offer Live Support for your website without forking out money every month? BlueSmiley offers it for free.
· Social Bookmarking: Share your bookmarks on your personal webpage.
· You can also show RSS Feeds within this Online Organize
What's New in This Release: [ read full changelog ]
· Various fixes (MySQL 5.5 support, a timezone fix, removal of deprecated PHP commands) and improvements: the search bar has 10 more slots, and to-do has a new status field.
Team Fortress 2 Skin - Scout's Leg Bandage
If you are looking for a cool new Scout skin for the world of Team Fortress 2 you can try the latest Scout's Leg Bandage skin pack.
Change some of the default skins in Team Fortress 2 you using this new skin pack.
Requirements:
· Team Fortress 2
Wednesday, June 19, 2013
Team Fortress 2 Skin - Nature Sniper v2
Try this new skin pack and change some of the default skins in Team Fortress 2 for an improved game experience.
Requirements:
· Team Fortress 2
View the original article here
Super Gerball 1.1
Your job is made harder by the numerous obstacles left lying about - if Gerry touches these, he will be pushed away - and possibly off an edge.
There is also a time limit to contend with - Gerry must complete all the levels by midnight. If Gerry completes a level, he will dance a jig in celebration.
It is up to you to make sure he dances all day long - and is still dancing at the end of the night. Feel like playing along?
Here are some key features of "Super Gerball":
· 60 levels - 60 fun, exciting levels provide a long-lasting challenge
· 6 game zones - Super Gerball provides you with the ultimate in graphical variety
· 3 high score tables - compete against friends and family to see who is the best
· 3 unique endings - complete the game in easy, medium or hard mode and you will be rewarded with an entertaining end sequence
Requirements:
· 750Mhz Intel or AMD processor
· Windows 95/98/ME/2000/XP
· DirectX 7.0 or newer
· Direct3D compatible video chipset
Limitations:
· The trial version has fewer levels to play.
View the original article here
GTA IV Addon - Honda Civic Anil Tuning
After unpacking the archive, you must copy the content in the following path: Rockstar Games/GTA IV/Models.
Requirements:
· Grand Theft Auto IV
View the original article here
Fluffy Adventure
You must guide a fuzzy character through a world filled with fairies while avoiding endless pits and lots of enemies. With each fruit and vegetable you collect, points will be added. Use the WASD keys to move.
Here are some key features of "Fluffy Adventure":
· Cute little kitty
· Classic gameplay
· Funny sound effects
Requirements:
· Windows XP/Vista/7/8
· Processor 800 Mhz or better
· 512 Mb RAM
· DirectX 8.1
Users are advised to pay attention while installing this ad-supported application:
· Displays ad banners or other types of advertising material during its runtime.
· Attempts to change the homepage for web browsers installed on the system.
· Attempts to change the default search engine for web browsers installed on the system.
View the original article here
Call of Juarez: Gunslinger +7 Trainer for 1.02
NOTE: This new trainer is for the 1.02 version of the game!
View the original article here
Team Fortress 2 Skin - IC Spy V2
Try this new skin pack and change some of the default skins in Team Fortress 2 for an improved game experience.
Requirements:
· Team Fortress 2
View the original article here
Mexico arrests top 10 US fugitive
 Walter Lee Williams was arrested in Playa del Carmen, Mexico Mexican officials have arrested a former US university professor who is on the FBI's 10 Most Wanted list.
Walter Lee Williams was arrested in Playa del Carmen, Mexico Mexican officials have arrested a former US university professor who is on the FBI's 10 Most Wanted list. Walter Lee Williams, 64, is facing charges of sexual exploitation of children and travelling to the Philippines to engage in sexual activity with minors.
He was arrested in the beach resort of Playa del Carmen, on Mexico's Caribbean coast.
He taught gender studies at the University of Southern California.
Local prosecutor Armando Garcia said police had detained Walter Lee Williams in a cafe in Playa del Carmen, 70km (43 miles) south of the town of Cancun.
On Monday, Walter Lee Williams had become the 500th fugitive to be named to the FBI's 10 most wanted list.
According to the FBI, the list has been key in galvanising public support to catch many of the people it deems "the nation's worst offenders".
The Bureau says that of the 500 fugitives who have been named to the list since it was first created 63 years ago, 469 have been apprehended or located.
"This has been a tremendously successful program, but one that is dependent on the willingness of concerned citizens with information to come forward and offer us their assistance," Ron Hosko of the FBI's criminal investigative division said.
The FBI had offered a reward of up to $100,000 (£64,000) for information leading directly to the arrest of Walter Lee Williams.
The Mexican authorities did not say how they had located Walter Lee Williams or if the reward would be paid out.
QUESTION NO: 1
Both switches and hubs are being utilized within the TestKing network.
Which of the following is true regarding the use of switches and hubs for
network connectivity in this network?
A. Switches take less time to process frames than hubs take
B. Hubs can filter frames
C. Switches do not forward broadcasts
D. Switches increase the number of collision domains in the network
E. Using hubs can increase the amount of bandwidth available to hosts
F. None of the above
Answer: D
QUESTION NO: 2
Which one of the following characteristics is true regarding the use of hubs
and switches?
A. Hubs can have their ports be configured with VLANs
B. Using hubs is costly with regard to bandwidth availability.
C. Switches can not forward broadcasts.
D. Switches are more efficient than hubs in processing frames.
E. Switches increase the number of collision domains in the network.
Answer: E
Switches increases the number of collisions domains in the network. Switches that are
configured with VLANs will reduce the size of the collision domains by increasing the
number of collision domains in a network, but making them smaller than that of one big,
flat network.
Incorrect Answers:
A. Switches are capable of VLAN configurations, but hubs are not.
B. Hubs are generally the least costly method possible to connect multiple devices together in a
network.
C. Switches forward broadcasts and multicasts, by default, to all ports within the same VLAN.
Only routers block all broadcast traffic by default.
D. Switches and hubs can be equally efficient in processing frames, in theory. In practice,
switches are generally more efficient as they usually have more CPU and memory allocated to
them, and are generally much more expensive than a simple hub.
QUESTION NO: 3
When comparing and contrasting the similarities and differences between
bridges and switches, which of the following are valid statements? Choose
all the valid answer choices)
A. Bridges are faster than switches because they have fewer ports.
B. A switch is a multiport bridge,
2
C. Bridges and switches learn MAC addresses by examining the source MAC
address of each frame received.
D. A bridge will forward a broadcast but a switch will not.
E. Bridges and switches increase the size of a collision domain.
F. None of the above statements are true.
Answer: B, C
Explanation:
Both bridges and switches build the bridge table by listening to incoming frames and examining
the source MAC address in the frame.
Switches are multiport bridges that allow you to create multiple broadcast domains. Each
broadcast domain is like a distinct virtual bridge within a switch.
Incorrect Answers:
A. Switches are generally faster than bridges. Bridges also do not necessarily have fewer ports
than switches.
D. Both bridges and switches will forward broadcast and multicast traffic, assuming that the traffic
remains in the same VLAN.
QUESTION NO: 4
Which of the following correctly describe the various functions and virtues
of a router? (Select all valid answer choices)
A. Packet switching
B. Collision prevention on a LAN segment.
C. Packet filtering
D. Broadcast domain enlargement
E. Broadcast forwarding
F. Internetwork communication
G. None of the above
Answer: A, C, F
Explanation:
The main function of a router is to connect different, separated networks together. In doing so,
switching packets from one network to another is a primary function, along with providing for
communication between networks. As an additional feature, routers are capable of providing
filtering on a network address and application port level, so choice C is also correct.
Incorrect Answers:
B. Routers can indeed be used to segment a network separate a collision domain, since routers
do not forward LAN broadcasts and multicasts to other interfaces. However, routers alone can not
prevent all collisions from occurring on any given LAN segment.
D. Routers actually segment LANs into smaller broadcast domains.
E. Routers do not forward broadcast and multicast traffic out the additional interfaces by default.
Unless bridging or IP helpers are configured on the router, LAN broadcasts are blocked at the
router level.
QUESTION NO: 5
3
The LAN needs are expanding at the Testking corporate office, which is
quickly growing. You are instructed to enlarge the area covered by a single
LAN segment on the TestKing network. Which of the following are layer 1
devices that you can use? (Choose all that apply.)
A. A switch
B. A router
C. A network adapter card
D. A hub
E. A repeater
Answer: D, E
Explanation:
A hub simply repeats the electrical signal and makes no attempt to interpret the electrical signal
(layer 1) as a LAN frame (Layer 2). So, a hub actually performs OSI layer 1 functions, repeating
an electrical signal, whereas a switch performs OSI layer 2 functions, actually interpreting
Ethernet header information, particularly addresses, to make forwarding decisions. Hubs can be
used to increase the number of stations that can be supported on a LAN.
Because the repeater does not interpret what the bits mean, but does examine and generate
electrical signals, a repeater is considered to operate at Layer 1. Repeaters can be used to
physically extend the LAN to greater distances.
QUESTION NO: 6
Both bridges are switches are being used throughout the TestKing LAN.
Which of the following statements are true regarding bridges and switches
in this network?
(Choose 3)
A. Switches are primarily software based while bridges are hardware based.
B. Switches usually have a higher number of ports than most bridges.
C. Bridges are frequently faster than switches.
D. Bridges define broadcast domains while switches define collision domains.
E. Both bridges and switches forward Layer 2 broadcasts.
F. Both bridges and switches make forwarding decisions based on Layer 2
addresses.
Answer: B, E, F
Friday, March 15, 2013
All About FTP
Setting Up A Ftp:
Well, since many of us have always wondered this, here it is. Long and drawn out. Also, before attempting this, realize one thing; You will have to give up your time, effort, bandwidth, and security to have a quality ftp server.
That being said, here it goes. First of all, find out if your IP (Internet Protocol) is static (not changing) or dynamic (changes everytime you log on). To do this, first consider the fact if you have a dial up modem. If you do, chances are about 999 999 out of 1 000 000 that your IP is dynamic. To make it static, just go to a place like h*tp://www.myftp.org/ to register for a static ip address.
You'll then need to get your IP. This can be done by doing this:
Going to Start -> Run -> winipcfg or www.ask.com and asking 'What is my IP?'
After doing so, you'll need to download an FTP server client. Personally, I'd recommend G6 FTP Server, Serv-U FTPor Bullitproof v2.15 all three of which are extremely reliable, and the norm of the ftp world.
You can download them on this site: h*tp://www.liaokai.com/softw_en/d_index.htm
First, you'll have to set up your ftp. For this guide, I will use step-by-step instructions for G6. First, you'll have to go into 'Setup -> General'. From here, type in your port # (default is 21). I recommend something unique, or something a bit larger (ex: 3069). If you want to, check the number of max users (this sets the amount of simultaneous maximum users on your server at once performing actions - The more on at once, the slower the connection and vice versa).
The below options are then chooseable:
-Launch with windows
-Activate FTP Server on Start-up
-Put into tray on startup
-Allow multiple instances
-Show "Loading..." status at startup
-Scan drive(s) at startup
-Confirm exit
You can do what you want with these, as they are pretty self explanatory. The scan drive feature is nice, as is the 2nd and the last option. From here, click the 'options' text on the left column.
To protect your server, you should check 'login check' and 'password check', 'Show relative path (a must!)', and any other options you feel you'll need. After doing so, click the 'advanced' text in the left column. You should then leave the buffer size on the default (unless of course you know what you're doing ), and then allow the type of ftp you want.
Uploading and downloading is usually good, but it's up to you if you want to allow uploads and/or downloads. For the server priority, that will determine how much conventional memory will be used and how much 'effort' will go into making your server run smoothly.
Anti-hammering is also good, as it prevents people from slowing down your speed. From here, click 'Log Options' from the left column. If you would like to see and record every single command and clutter up your screen, leave the defaults.
But, if you would like to see what is going on with the lowest possible space taken, click 'Screen' in the top column. You should then check off 'Log successful logins', and all of the options in the client directry, except 'Log directory changes'. After doing so, click 'Ok' in the bottom left corner.
You will then have to go into 'Setup -> User Accounts' (or ctrl & u). From here, you should click on the right most column, and right click. Choose 'Add', and choose the username(s) you would like people to have access to.
After giving a name (ex: themoonlanding), you will have to give them a set password in the bottom column (ex: wasfaked). For the 'Home IP' directory, (if you registered with a static server, check 'All IP Homes'. If your IP is static by default, choose your IP from the list. You will then have to right click in the very center column, and choose 'Add'.
From here, you will have to set the directory you want the people to have access to. After choosing the directory, I suggest you choose the options 'Read', 'List', and 'Subdirs', unless of course you know what you're doing . After doing so, make an 'upload' folder in the directory, and choose to 'add' this folder seperately to the center column. Choose 'write', 'append', 'make', 'list', and 'subdirs'. This will allow them to upload only to specific folders (your upload folder).
Now click on 'Miscellaneous' from the left column. Choose 'enable account', your time-out (how long it takes for people to remain idle before you automatically kick them off), the maximum number of users for this name, the maximum number of connections allowed simultaneously for one ip address, show relative path (a must!), and any other things at the bottom you'd like to have. Now click 'Ok'.
**Requested**
From this main menu, click the little boxing glove icon in the top corner, and right click and unchoose the hit-o-meter for both uploads and downloads (with this you can monitor IP activity). Now click the lightning bolt, and your server is now up and running.
Post your ftp info, like this:
213.10.93.141 (or something else, such as: 'f*p://example.getmyip.com')
User: *** (The username of the client)
Pass: *** (The password)
Port: *** (The port number you chose)
So make a FTP and join the FTP section
Listing The Contents Of A Ftp:
Listing the content of a FTP is very simple.
You will need FTP Content Maker, which can be downloaded from here:
ht*p://www.etplanet.com/download/application/FTP%20Content%20Maker%201.02.zip
1. Put in the IP of the server. Do not put "ftp://" or a "/" because it will not work if you do so.
2. Put in the port. If the port is the default number, 21, you do not have to enter it.
3. Put in the username and password in the appropriate fields. If the login is anonymous, you do not have to enter it.
4. If you want to list a specific directory of the FTP, place it in the directory field. Otherwise, do not enter anything in the directory field.
5. Click "Take the List!"
6. After the list has been taken, click the UBB output tab, and copy and paste to wherever you want it.
If FTP Content Maker is not working, it is probably because the server does not utilize Serv-U Software.
If you get this error message:
StatusCode = 550
LastResponse was : 'Unable to open local file test-ftp'
Error = 550 (Unable to open local file test-ftp)
Error = Unable to open local file test-ftp = 550
Close and restart FTP Content Maker, then try again.
error messages:
110 Restart marker reply. In this case, the text is exact and not left to the particular implementation; it must read: MARK yyyy = mmmm Where yyyy is User-process data stream marker, and mmmm server's equivalent marker (note the spaces between markers and "=").
120 Service ready in nnn minutes.
125 Data connection already open; transfer starting.
150 File status okay; about to open data connection.
200 Command okay.
202 Command not implemented, superfluous at this site.
211 System status, or system help reply.
212 Directory status.
213 File status.
214 Help message. On how to use the server or the meaning of a particular non-standard command. This reply is useful only to the human user.
215 NAME system type. Where NAME is an official system name from the list in the Assigned Numbers document.
220 Service ready for new user.
221 Service closing control connection. Logged out if appropriate.
225 Data connection open; no transfer in progress.
226 Closing data connection. Requested file action successful (for example, file transfer or file abort).
227 Entering Passive Mode (h1,h2,h3,h4,p1,p2).
230 User logged in, proceed.
250 Requested file action okay, completed.
257 "PATHNAME" created.
331 User name okay, need password.
332 Need account for login.
350 Requested file action pending further information.
421 Too many users logged to the same account
425 Can't open data connection.
426 Connection closed; transfer aborted.
450 Requested file action not taken. File unavailable (e.g., file busy).
451 Requested action aborted: local error in processing.
452 Requested action not taken. Insufficient storage space in system.
500 Syntax error, command unrecognized. This may include errors such as command line too long.
501 Syntax error in parameters or arguments.
502 Command not implemented.
503 Bad sequence of commands.
504 Command not implemented for that parameter.
530 Not logged in.
532 Need account for storing files.
550 Requested action not taken. File unavailable (e.g., file not found, no access).
551 Requested action aborted: page type unknown.
552 Requested file action aborted. Exceeded storage allocation (for current directory or dataset).
553 Requested action not taken. File name not allowed.
Active FTP vs. Passive FTP, a Definitive Explanation
Introduction
One of the most commonly seen questions when dealing with firewalls and other Internet connectivity issues is the difference between active and passive FTP and how best to support either or both of them. Hopefully the following text will help to clear up some of the confusion over how to support FTP in a firewalled environment.
This may not be the definitive explanation, as the title claims, however, I've heard enough good feedback and seen this document linked in enough places to know that quite a few people have found it to be useful. I am always looking for ways to improve things though, and if you find something that is not quite clear or needs more explanation, please let me know! Recent additions to this document include the examples of both active and passive command line FTP sessions. These session examples should help make things a bit clearer. They also provide a nice picture into what goes on behind the scenes during an FTP session. Now, on to the information...
The Basics
FTP is a TCP based service exclusively. There is no UDP component to FTP. FTP is an unusual service in that it utilizes two ports, a 'data' port and a 'command' port (also known as the control port). Traditionally these are port 21 for the command port and port 20 for the data port. The confusion begins however, when we find that depending on the mode, the data port is not always on port 20.
Active FTP
In active mode FTP the client connects from a random unprivileged port (N > 1024) to the FTP server's command port, port 21. Then, the client starts listening to port N+1 and sends the FTP command PORT N+1 to the FTP server. The server will then connect back to the client's specified data port from its local data port, which is port 20.
From the server-side firewall's standpoint, to support active mode FTP the following communication channels need to be opened:
FTP server's port 21 from anywhere (Client initiates connection)
FTP server's port 21 to ports > 1024 (Server responds to client's control port)
FTP server's port 20 to ports > 1024 (Server initiates data connection to client's data port)
FTP server's port 20 from ports > 1024 (Client sends ACKs to server's data port)
In step 1, the client's command port contacts the server's command port and sends the command PORT 1027. The server then sends an ACK back to the client's command port in step 2. In step 3 the server initiates a connection on its local data port to the data port the client specified earlier. Finally, the client sends an ACK back as shown in step 4.
The main problem with active mode FTP actually falls on the client side. The FTP client doesn't make the actual connection to the data port of the server--it simply tells the server what port it is listening on and the server connects back to the specified port on the client. From the client side firewall this appears to be an outside system initiating a connection to an internal client--something that is usually blocked.
Active FTP Example
Below is an actual example of an active FTP session. The only things that have been changed are the server names, IP addresses, and user names. In this example an FTP session is initiated from testbox1.slacksite.com (192.168.150.80), a linux box running the standard FTP command line client, to testbox2.slacksite.com (192.168.150.90), a linux box running ProFTPd 1.2.2RC2. The debugging (-d) flag is used with the FTP client to show what is going on behind the scenes. Everything in red is the debugging output which shows the actual FTP commands being sent to the server and the responses generated from those commands. Normal server output is shown in black, and user input is in bold.
There are a few interesting things to consider about this dialog. Notice that when the PORT command is issued, it specifies a port on the client (192.168.150.80) system, rather than the server. We will see the opposite behavior when we use passive FTP. While we are on the subject, a quick note about the format of the PORT command. As you can see in the example below it is formatted as a series of six numbers separated by commas. The first four octets are the IP address while the second two octets comprise the port that will be used for the data connection. To find the actual port multiply the fifth octet by 256 and then add the sixth octet to the total. Thus in the example below the port number is ( (14*256) + 178), or 3762. A quick check with netstat should confirm this information.
testbox1: {/home/p-t/slacker/public_html} % ftp -d testbox2
Connected to testbox2.slacksite.com.
220 testbox2.slacksite.com FTP server ready.
Name (testbox2:slacker): slacker
---> USER slacker
331 Password required for slacker.
Password: TmpPass
---> PASS XXXX
230 User slacker logged in.
---> SYST
215 UNIX Type: L8
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
ftp: setsockopt (ignored): Permission denied
---> PORT 192,168,150,80,14,178
200 PORT command successful.
---> LIST
150 Opening ASCII mode data connection for file list.
drwx------ 3 slacker users 104 Jul 27 01:45 public_html
226 Transfer complete.
ftp> quit
---> QUIT
221 Goodbye.
Passive FTP
In order to resolve the issue of the server initiating the connection to the client a different method for FTP connections was developed. This was known as passive mode, or PASV, after the command used by the client to tell the server it is in passive mode.
In passive mode FTP the client initiates both connections to the server, solving the problem of firewalls filtering the incoming data port connection to the client from the server. When opening an FTP connection, the client opens two random unprivileged ports locally (N > 1024 and N+1). The first port contacts the server on port 21, but instead of then issuing a PORT command and allowing the server to connect back to its data port, the client will issue the PASV command. The result of this is that the server then opens a random unprivileged port (P > 1024) and sends the PORT P command back to the client. The client then initiates the connection from port N+1 to port P on the server to transfer data.
From the server-side firewall's standpoint, to support passive mode FTP the following communication channels need to be opened:
FTP server's port 21 from anywhere (Client initiates connection)
FTP server's port 21 to ports > 1024 (Server responds to client's control port)
FTP server's ports > 1024 from anywhere (Client initiates data connection to random port specified by server)
FTP server's ports > 1024 to remote ports > 1024 (Server sends ACKs (and data) to client's data port)
In step 1, the client contacts the server on the command port and issues the PASV command. The server then replies in step 2 with PORT 2024, telling the client which port it is listening to for the data connection. In step 3 the client then initiates the data connection from its data port to the specified server data port. Finally, the server sends back an ACK in step 4 to the client's data port.
While passive mode FTP solves many of the problems from the client side, it opens up a whole range of problems on the server side. The biggest issue is the need to allow any remote connection to high numbered ports on the server. Fortunately, many FTP daemons, including the popular WU-FTPD allow the administrator to specify a range of ports which the FTP server will use. See Appendix 1 for more information.
The second issue involves supporting and troubleshooting clients which do (or do not) support passive mode. As an example, the command line FTP utility provided with Solaris does not support passive mode, necessitating a third-party FTP client, such as ncftp.
With the massive popularity of the World Wide Web, many people prefer to use their web browser as an FTP client. Most browsers only support passive mode when accessing ftp:// URLs. This can either be good or bad depending on what the servers and firewalls are configured to support.
Passive FTP Example
Below is an actual example of a passive FTP session. The only things that have been changed are the server names, IP addresses, and user names. In this example an FTP session is initiated from testbox1.slacksite.com (192.168.150.80), a linux box running the standard FTP command line client, to testbox2.slacksite.com (192.168.150.90), a linux box running ProFTPd 1.2.2RC2. The debugging (-d) flag is used with the FTP client to show what is going on behind the scenes. Everything in red is the debugging output which shows the actual FTP commands being sent to the server and the responses generated from those commands. Normal server output is shown in black, and user input is in bold.
Notice the difference in the PORT command in this example as opposed to the active FTP example. Here, we see a port being opened on the server (192.168.150.90) system, rather than the client. See the discussion about the format of the PORT command above, in the Active FTP Example section.
testbox1: {/home/p-t/slacker/public_html} % ftp -d testbox2
Connected to testbox2.slacksite.com.
220 testbox2.slacksite.com FTP server ready.
Name (testbox2:slacker): slacker
---> USER slacker
331 Password required for slacker.
Password: TmpPass
---> PASS XXXX
230 User slacker logged in.
---> SYST
215 UNIX Type: L8
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> passive
Passive mode on.
ftp> ls
ftp: setsockopt (ignored): Permission denied
---> PASV
227 Entering Passive Mode (192,168,150,90,195,149).
---> LIST
150 Opening ASCII mode data connection for file list
drwx------ 3 slacker users 104 Jul 27 01:45 public_html
226 Transfer complete.
ftp> quit
---> QUIT
221 Goodbye.
Summary
The following chart should help admins remember how each FTP mode works:
Active FTP :
command : client >1024 -> server 21
data : client >1024 <- server 20
Passive FTP :
command : client >1024 -> server 21
data : client >1024 -> server >1024
A quick summary of the pros and cons of active vs. passive FTP is also in order:
Active FTP is beneficial to the FTP server admin, but detrimental to the client side admin. The FTP server attempts to make connections to random high ports on the client, which would almost certainly be blocked by a firewall on the client side. Passive FTP is beneficial to the client, but detrimental to the FTP server admin. The client will make both connections to the server, but one of them will be to a random high port, which would almost certainly be blocked by a firewall on the server side.
Luckily, there is somewhat of a compromise. Since admins running FTP servers will need to make their servers accessible to the greatest number of clients, they will almost certainly need to support passive FTP. The exposure of high level ports on the server can be minimized by specifying a limited port range for the FTP server to use. Thus, everything except for this range of ports can be firewalled on the server side. While this doesn't eliminate all risk to the server, it decreases it tremendously.
written by unknown
Tuesday, March 12, 2013
Phone Systems Tutorial by The Jolly Roger
To start off, we will discuss the dialing procedures for domestic
as well as international dialing. We will also take a look at the
telephone numbering plan.
North American Numbering Plan
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In North America, the telephone numbering plan is as follows:
A) a 3 digit Numbering Plan Area (NPA) code , ie, area code
B) a 7 digit telephone # consisting of a 3 digit Central Office
(CO) code plus a 4 digit station #
These 10 digits are called the network address or destination
code. It is in the format of:
Area Code Telephone #
--------- -----------
N*X NXX-XXXX
Where: N = a digit from 2 to 9
* = the digit 0 or 1
X = a digit from 0 to 9
Area Codes
~~~~~~~~~~
Check your telephone book or the seperate listing of area codes
found on many bbs's. Here are the special area codes (SAC's):
510 - TWX (USA)
610 - TWX (Canada)
700 - New Service
710 - TWX (USA)
800 - WATS
810 - TWX (USA)
900 - DIAL-IT Services
910 - TWX (USA)
The other area codes never cross state lines, therefore each state
must have at least one exclusive NPA code. When a community is
split by a state line, the CO #'s are often interchangeable (ie,
you can dial the same number from two different area codes).
TWX (Telex II) consists of 5 teletype-writer area codes. They are
owned by Western Union. These SAC's may only be reached via other
TWX machines. These run at 110 baud (last I checked! They are most
likely faster now!). Besides the TWX #'s, these machines are
routed to normal telephone #'s. TWX machines always respond with
an answerback. For example, WU's FYI TWX # is (910) 279-5956. The
answerback for this service is "WU FYI MAWA".
If you don't want to but a TWX machine, you can still send TWX
messages using Easylink [800/325-4112]. However you are gonna have
to hack your way onto this one!
700:
700 is currently used by AT&T as a call forwarding service. It is
targeted towards salesmen on the run. To understand how this
works, I'll explain it with an example. Let's say Joe Q. Salespig
works for AT&T security and he is on the run chasing a phreak
around the country who royally screwed up an important COSMOS
system. Let's say that Joe's 700 # is (700) 382-5968. Everytime
Joe goes to a new hotel (or most likely SLEAZY MOTEL), he dials a
special 700 #, enters a code, and the number where he is staying.
Now, if his boss received some important info, all he would do is
dial (700) 382-5968 and it would ring wherever Joe last progammed
it to. Neat, huh?
800:
This SAC is one of my favourites since it allows for toll free
calls. INWARD WATS (INWATS), or Inward Wide Area
Telecommunications Service is the 800 #'s that we are all familiar
with. 800 #'s are set up in service areas or bands. There are 6 of
these. Band 6 is the largest and you can call a band 6 # from
anywhere in the US except the state where the call is terminated
(that is why most companies have one 800 number for the countery
and then another one for their state.) Band 5 includes the 48
contiguous states. All the way down to band 1 which includes only
the states contiguous to that one. Therefore, less people can
reach a band 1 INWATS # than a band 6 #.
Intrastate INWATS #'s (ie, you can call it from only 1 state)
always have a 2 as the last digit in the exchange (ie, 800-NX2-
XXXX). The NXX on 800 #'s represent the area where the business is
located. For example, a # beginning with 800-431 would terminate
at a NY CO.
800 #'s always end up in a hunt series in a CO. This means that it
tries the first # allocated to the company for their 800 lines; if
this is busy, it will try the next #, etc. You must have a minimum
of 2 lines for each 800 #. For example, Travelnet uses a hunt
series. If you dial (800) 521-8400, it will first try the #
associated with 8400; if it is busy it will go to the next
available port, etc. INWATS customers are billed by the number of
hours of calls made to their #.
OUTWATS (OUTWARD WATS): OUTWATS are for making outgoing calls
only. Largecompanies use OUTWATS since they receive bulk-rate
discounts. Since OUTWATS numbers cannot have incoming calls, they
are in the format of:
(800) *XXX-XXXX
Where * is the digit 0 or 1 (or it may even be designated by a
letter) which cannot be dialed unless you box the call. The *XX
identifies the type of service and the areas that the company can
call.
Remember:
INWATS + OUTWATS = WATS EXTENDER
900:
This DIAL-IT SAC is a nationwide dial-it service. It is use for
taking television polls and other stuff. The first minute
currently costs an outrageous 50-85 cents and each additional
minute costs 35-85 cents. Hell takes in a lot of revenue this way!
Dial (900) 555-1212 to find out what is currently on this service.
CO CODES
~~~~~~~~
These identify the switching office where the call is to be
routed. The following CO codes are reserved nationwide:
555 - directory assistance
844 - time. These are now in!
936 - weather the 976 exchange
950 - future services
958 - plant test
959 - plant test
970 - plant test (temporary)
976 - DIAL-IT services
Also, the 3 digit ANI & ringback #'s are regarded as plant test
and are thus reserved. These numbers vary from area to area.
You cannot dial a 0 or 1 as the first digit of the exchange code
(unless using a blue box!). This is due to the fact that these
exchanges (000-199) contains all sorts of interesting shit such as
conference #'s, operators, test #'s, etc.
950:
Here are the services that are currently used by the 950 exchange:
1000 - SPC
1022 - MCI Execunet
1033 - US Telephone
1044 - Allnet
1066 - Lexitel
1088 - SBS Skyline
These SCC's (Specialized Common Carriers) are free from fortress
phones! Also, the 950 exchange will probably be phased out with
the introduction of Equal Access
Plant Tests:
These include ANI, Ringback, and other various tests.
976:
Dial 976-1000 to see what is currently on the service. Also, many
bbs's have listings of these numbers.
N11 codes:
----------
Bell is trying to phase out some of these, but they still exist in
most areas.
011 - international dialing prefix
211 - coin refund operator
411 - directory assistance
611 - repair service
811 - business office
911 - EMERGENCY
International Dialing
~~~~~~~~~~~~~~~~~~~~~
With International Dialing, the world has been divided into 9
numbering zones. To make an international call, you must first
dial: International Prefix + Country code + National #
In North America, the international dialing prefix is 011 for
station-to-station calls. If you can dial International #'s
directly in your area then you have International Direct Distance
Dialing (IDDD).
The country code, which varies from 1 to 3 digits, always has the
world numbering zone as the first digit. For example, the country
code for the United Kingdom is 44, thus it is in world numbering
zone 4. Some boards may contain a complete listing of other
country codes, but here I give you a few:
1 - North America (US, Canada, etc.)
20 - Egypt
258 - Mozambique
34 - Spain
49 - Germany
52 - Mexico (southern portion)
7 - USSR
81 - Japan
98 - Iran (call & hassle those bastards!)
If you call from an area other than North America, the format is
generally the same. For example, let's say that you wanted to call
the White House from Switzerland to tell the prez that his
numbered bank account is overdrawn (it happens, you know! ha ha).
First you would dial 00 (the SWISS international dialing refix),
then 1 (the US country code), followed by 202-456-1414 (the
national # for the White House. Just ask for Georgy and give him
the bad news!)
Also, country code 87 is reserved for Maritime mobile service, ie,
calling ships:
871 - Marisat (Atlantic)
871 - Marisat (Pacific)
872 - Marisat (Indian)
International Switching:
------------------------
In North America there are currently 7 no. 4 ESS's that perform
the duty of ISC (Inter-nation Switching Centers). All
international calls dialed from numbering zone 1 will be routed
through one of these "gateway cities". They are:
182 - White Plains, NY
183 - New York, NY
184 - Pittsburgh, PA
185 - Orlando, Fl
186 - Oakland, CA
187 - Denver, CO
188 - New York, NY
The 18X series are operator routing codes for overseas access (to
be furthur discussed with blue boxes). All international calls use
a signaling service called CCITT.It is an international standard
for signaling.
Ok.. there you go for now! If you wanna read more about this, read
part two which is the next file #36 in the Jolly Roger's cookbook!
Picking Master Locks by The Jolly Roger
Have you ever tried to impress someone by picking one of those
Master combination locks and failed?
The Master lock company made their older combination locks with a
protection scheme. If you pull the handle too hard, the knob will
not turn. That was their biggest mistake.
The first number:
Get out any of the Master locks so you know what is going on.
While pulling on the clasp (part that springs open when you get
the combination right), turn the knob to the left until it will
not move any more, and add five to the number you reach. You now
have the first number of the combination.
The second number:
Spin the dial around a couple of times, then go to the first
number you got. Turn the dial to the right, bypassing the first
number once. When you have bypassed the first number, start
pulling on the clasp and turning the knob. The knob will
eventually fall into the groove and lock. While in the groove,
pull the clasp and turn the knob. If the knob is loose, go to the
next groove, if the knob is stiff, you have the second number of
the combination.
The third number:
After getting the second number, spin the dial, then enter the two
numbers. Slowly spin the dial to the right, and at each number,
pull on the clasp. The lock will eventually open if you did the
process right.
This method of opening Master locks only works on older models.
Someone informed Master of their mistake, and they employed a new
mechanism that is foolproof (for now).
The older models are from 1988-1990. The newer models are being
cracked on as we speak..
How Linux Booting Happens
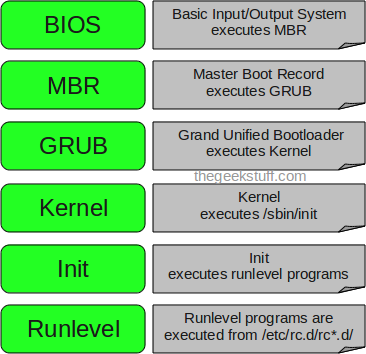
boot process:
1. A boot loader finds the kernel image on the disk, loads it into memory, and starts it.
2. The kernel initializes the devices and its drivers.
3. The kernel mounts the root filesystem.
4. The kernel starts a program called init.
5. init sets the rest of the processes in motion.
6. The last processes that init starts as part of the boot sequence allow you to log in.
Identifying each stage of the boot process is invaluable in fixing boot problems and understanding the system as a whole. To start, zero in on the boot loader, which is the initial screen or prompt you get after the computer does its power-on self-test, asking which operating system to run. After you make a choice, the boot loader runs the Linux kernel, handing control of the system to the kernel.
There is a detailed discussion of the kernel elsewhere in this book from which this article is excerpted. This article covers the kernel initialization stage, the stage when the kernel prints a bunch of messages about the hardware present on the system. The kernel starts init just after it displays a message proclaiming that the kernel has mounted the root filesystem:
VFS: Mounted root (ext2 filesystem) readonly.
Soon after, you will see a message about init starting, followed by system service startup messages, and finally you get a login prompt of some sort.
NOTE On Red Hat Linux, the init note is especially obvious, because it "welcomes" you to "Red Hat Linux." All messages thereafter show success or failure in brackets at the right-hand side of the screen.
Most of this chapter deals with init, because it is the part of the boot sequence where you have the most control.
init
There is nothing special about init. It is a program just like any other on the Linux system, and you'll find it in /sbin along with other system binaries. The main purpose of init is to start and stop other programs in a particular sequence. All you have to know is how this sequence works.
There are a few different variations, but most Linux distributions use the System V style discussed here. Some distributions use a simpler version that resembles the BSD init, but you are unlikely to encounter this.
Runlevels
At any given time on a Linux system, a certain base set of processes is running. This state of the machine is called its runlevel, and it is denoted with a number from 0 through 6. The system spends most of its time in a single runlevel. However, when you shut the machine down, init switches to a different runlevel in order to terminate the system services in an orderly fashion and to tell the kernel to stop. Yet another runlevel is for single-user mode, discussed later.
The easiest way to get a handle on runlevels is to examine the init configuration file, /etc/inittab. Look for a line like the following:
id:5:initdefault:
This line means that the default runlevel on the system is 5. All lines in the inittab file take this form, with four fields separated by colons occurring in the following order:
# A unique identifier (a short string, such as id in the preceding example)
# The applicable runlevel number(s)
# The action that init should take (in the preceding example, the action is to set the default runlevel to 5)
# A command to execute (optional)
There is no command to execute in the preceding initdefault example because a command doesn't make sense in the context of setting the default runlevel. Look a little further down in inittab, until you see a line like this:
l5:5:wait:/etc/rc.d/rc 5
This line triggers most of the system configuration and services through the rc*.d and init.d directories. You can see that init is set to execute a command called /etc/rc.d/rc 5 when in runlevel 5. The wait action tells when and how init runs the command: run rc 5 once when entering runlevel 5, and then wait for this command to finish before doing anything else.
There are several different actions in addition to initdefault and wait, especially pertaining to power management, and the inittab(5) manual page tells you all about them. The ones that you're most likely to encounter are explained in the following sections.
respawn
The respawn action causes init to run the command that follows, and if the command finishes executing, to run it again. You're likely to see something similar to this line in your inittab file:
1:2345:respawn:/sbin/mingetty tty1
The getty programs provide login prompts. The preceding line is for the first virtual console (/dev/tty1), the one you see when you press ALT-F1 or CONTROL-ALT-F1. The respawn action brings the login prompt back after you log out.
ctrlaltdel
The ctrlaltdel action controls what the system does when you press CONTROL-ALT-DELETE on a virtual console. On most systems, this is some sort of reboot command using the shutdown command.
sysinit
The sysinit action is the very first thing that init should run when it starts up, before entering any runlevels.
How processes in runlevels start
You are now ready to learn how init starts the system services, just before it lets you log in. Recall this inittab line from earlier:
l5:5:wait:/etc/rc.d/rc 5
This small line triggers many other programs. rc stands for run commands, and you will hear people refer to the commands as scripts, programs, or services. So, where are these commands, anyway?
For runlevel 5, in this example, the commands are probably either in /etc/rc.d/rc5.d or /etc/rc5.d. Runlevel 1 uses rc1.d, runlevel 2 uses rc2.d, and so on. You might find the following items in the rc5.d directory:
S10sysklogd S20ppp S99gpm
S12kerneld S25netstd_nfs S99httpd
S15netstd_init S30netstd_misc S99rmnologin
S18netbase S45pcmcia S99sshd
S20acct S89atd
S20logoutd S89cron
The rc 5 command starts programs in this runlevel directory by running the following commands:
S10sysklogd start
S12kerneld start
S15netstd_init start
S18netbase start
...
S99sshd start
Notice the start argument in each command. The S in a command name means that the command should run in start mode, and the number (00 through 99) determines where in the sequence rc starts the command.
The rc*.d commands are usually shell scripts that start programs in /sbin or /usr/sbin. Normally, you can figure out what one of the commands actually does by looking at the script with less or another pager program.
You can start one of these services by hand. For example, if you want to start the httpd Web server program manually, run S99httpd start. Similarly, if you ever need to kill one of the services when the machine is on, you can run the command in the rc*.d directory with the stop argument (S99httpd stop, for instance).
Some rc*.d directories contain commands that start with K (for "kill," or stop mode). In this case, rc runs the command with the stop argument instead of start. You are most likely to encounter K commands in runlevels that shut the system down.
Adding and removing services
If you want to add, delete, or modify services in the rc*.d directories, you need to take a closer look at the files inside. A long listing reveals a structure like this:
lrwxrwxrwx . . . S10sysklogd -> ../init.d/sysklogd
lrwxrwxrwx . . . S12kerneld -> ../init.d/kerneld
lrwxrwxrwx . . . S15netstd_init -> ../init.d/netstd_init
lrwxrwxrwx . . . S18netbase -> ../init.d/netbase
...
The commands in an rc*.d directory are actually symbolic links to files in an init.d directory, usually in /etc or /etc/rc.d. Linux distributions contain these links so that they can use the same startup scripts for all runlevels. This convention is by no means a requirement, but it often makes organization a little easier.
To prevent one of the commands in the init.d directory from running in a particular runlevel, you might think of removing the symbolic link in the appropriate rc*.d directory. This does work, but if you make a mistake and ever need to put the link back in place, you might have trouble remembering the exact name of the link. Therefore, you shouldn't remove links in the rc*.d directories, but rather, add an underscore (_) to the beginning of the link name like this:
mv S99httpd _S99httpd
At boot time, rc ignores _S99httpd because it doesn't start with S or K. Furthermore, the original name is still obvious, and you have quick access to the command if you're in a pinch and need to start it by hand.
To add a service, you must create a script like the others in the init.d directory and then make a symbolic link in the correct rc*.d directory. The easiest way to write a script is to examine the scripts already in init.d, make a copy of one that you understand, and modify the copy.
When adding a service, make sure that you choose an appropriate place in the boot sequence to start the service. If the service starts too soon, it may not work, due to a dependency on some other service. For non-essential services, most systems administrators prefer numbers in the 90s, after most of the services that came with the system.
Linux distributions usually come with a command to enable and disable services in the rc*.d directories. For example, in Debian, the command is update-rc.d, and in Red Hat Linux, the command is chkconfig. Graphical user interfaces are also available. Using these programs helps keep the startup directories consistent and helps with upgrades.
HINT: One of the most common Linux installation problems is an improperly configured XFree86 server that flicks on and off, making the system unusable on console. To stop this behavior, boot into single-user mode and alter your runlevel or runlevel services. Look for something containing xdm, gdm, or kdm in your rc*.d directories, or your /etc/inittab.
Controlling init
Occasionally, you need to give init a little kick to tell it to switch runlevels, to re-read the inittab file, or just to shut down the system. Because init is always the first process on a system, its process ID is always 1.
You can control init with telinit. For example, if you want to switch to runlevel 3, use this command:
telinit 3
When switching runlevels, init tries to kill off any processes that aren't in the inittab file for the new runlevel. Therefore, you should be careful about changing runlevels.
When you need to add or remove respawning jobs or make any other change to the inittab file, you must tell init about the change and cause it to re-read the file. Some people use kill -HUP 1 to tell init to do this. This traditional method works on most versions of Unix, as long as you type it correctly. However, you can also run this telinit command:
telinit q
You can also use telinit s to switch to single-user mode.
Shutting down
init also controls how the system shuts down and reboots. The proper way to shut down a Linux machine is to use the shutdown command.
There are two basic ways to use shutdown. If you halt the system, it shuts the machine down and keeps it down. To make the machine halt immediately, use this command:
shutdown -h now
On most modern machines with reasonably recent versions of Linux, a halt cuts the power to the machine. You can also reboot the machine. For a reboot, use -r instead of -h.
The shutdown process takes several seconds. You should never reset or power off a machine during this stage.
In the preceding example, now is the time to shut down. This argument is mandatory, but there are many ways of specifying it. If you want the machine to go down sometime in the future, one way is to use +n, where n is the number of minutes shutdown should wait before doing its work. For other options, look at the shutdown(8) manual page.
To make the system reboot in 10 minutes, run this command:
shutdown -r +10
On Linux, shutdown notifies anyone logged on that the machine is going down, but it does little real work. If you specify a time other than now, shutdown creates a file called /etc/nologin. When this file is present, the system prohibits logins by anyone except the superuser.
When system shutdown time finally arrives, shutdown tells init to switch to runlevel 0 for a halt and runlevel 6 for a reboot. When init enters runlevel 0 or 6, all of the following takes place, which you can verify by looking at the scripts inside rc0.d and rc6.d:
1. init kills every process that it can (as it would when switching to any other runlevel).
# The initial rc0.d/rc6.d commands run, locking system files into place and making other preparations for shutdown.
# The next rc0.d/rc6.d commands unmount all filesystems other than the root.
# Further rc0.d/rc6.d commands remount the root filesystem read-only.
# Still more rc0.d/rc6.d commands write all buffered data out to the filesystem with the sync program.
# The final rc0.d/rc6.d commands tell the kernel to reboot or stop with the reboot, halt, or poweroff program.
The reboot and halt programs behave differently for each runlevel, potentially causing confusion. By default, these programs call shutdown with the -r or -h options, but if the system is already at the halt or reboot runlevel, the programs tell the kernel to shut itself off immediately. If you really want to shut your machine down in a hurry (disregarding any possible damage from a disorderly shutdown), use the -f option.